Imagine signing up for a gym that promises world-class equipment, 24/7 access, and personal trainers—only to find out that the treadmills are always broken, the sauna costs extra, and you need a PhD to use the weight machines. Now, replace “gym” with a Security Information and Event Management (SIEM) solution, and you have the reality that many businesses face when choosing a SIEM tool. There are too many features, too much fine print, and an ongoing battle with SIEM pricing models that seem designed to confuse.
So how do you avoid the wrong SIEM provider, cut through the jargon, and choose a SIEM smartly to get value for your investment? Let’s break it down.
Not Sure Which SIEM Fits Your Business?
5 Biggest SIEM Buying Mistakes
Buying a SIEM without a clear plan is like picking a car based on the number of cup holders—it might seem fine at first, but sooner or later, you’ll realize you’ve overlooked the features that matter.
We see companies waste time, money, and patience trying to get their SIEM to work the way they expected it to. They either go for the cheapest option, ignore the hidden costs, or choose something too complex for their team to handle. Here are the top mistakes we see—and how to dodge them before they become expensive regrets.
Mistake #1: Focusing only on price
Let’s be honest—SIEM solutions are expensive, and pricing is usually the first thing people look at. It’s tempting to go with the cheapest option, hoping to save money. Many companies start with Elastic because of its low initial cost—it’s open-source and seems like a great deal upfront.
But here’s the catch: low-cost SIEMs come with hidden expenses. Elastic is an attractive SIEM choice, especially for those looking for an open-source solution with low initial costs. However, as security needs grow, infrastructure expenses can rise quickly, scaling demands technical expertise, and ongoing maintenance requires significant resources. What starts as a budget-friendly option can evolve into a complex, engineering-heavy project, requiring a dedicated team to manage effectively.
Most of our customers with strong technical teams and DevOps-driven environments choose on-prem Elastic. If you lack a dedicated SIEM engineer, you might end up paying more in time, effort, and unexpected infrastructure costs.
Mistake #2: Ignoring scalability
Your security needs today won’t be the same in a year. SIEMs process massive amounts of data, and as your company grows, log volumes will explode. If your SIEM can’t scale smoothly, you’ll eventually hit performance bottlenecks, and delays, or be forced into an expensive migration.
As mentioned above, Elastic on-prem is a powerful SIEM, but scaling it isn’t simple. It often requires data reindexing and additional component modifications, which means more hands-on work for your security team. If you don’t plan for this from the start, what seems like a perfect fit today could turn into a major operational headache down the road.
If you expect your security needs to grow, choosing a SIEM that supports auto-scaling without heavy reconfiguration can save you time, money, and frustration.
Mistake #3: Underestimating the learning curve
Many SIEMs aren’t plug-and-play, and companies often underestimate the resources needed to keep them running effectively.
Take Elastic and Splunk—both are powerful, but both require dedicated security engineers to fine-tune detection rules, optimize performance, and ensure logs are useful.
This is where companies get stuck. They assume their IT team can handle it, only to realize weeks or months later that managing a SIEM is a full-time job. Suddenly, they’re drowning in alerts, struggling to configure rules, and spending hours maintaining a system that was supposed to make security easier.If your security team is already stretched thin, consider co-managed or fully managed SIEM services instead of trying to handle everything in-house. SIEM management isn’t just about installing the tool—it’s about ongoing tuning, threat detection, and response. Without the right expertise, you’re not getting the full value from your SIEM investment.

Mistake #4: Skipping integration compatibility
Your SIEM doesn’t work in isolation—it needs to connect seamlessly with your other security tools, cloud platforms, and compliance frameworks. But here’s where many companies get burned: SIEM vendors promise “easy integrations” that turn into API nightmares.
Elastic, for example, supports only 200+ security integrations, so if your business relies on a complex security ecosystem, choosing a SIEM with limited integrations will create more work for your team, not less. Our team prefers Splunk in case integrations is the factor
We’ve seen companies spend months troubleshooting SIEM integrations—fixing broken connectors, dealing with data inconsistencies, and manually ingesting logs because their SIEM wasn’t as “compatible” as they thought. If you don’t check integration support upfront, you might be in an endless cycle of patching, debugging, and frustration.
Mistake #5: Ignoring compliance & reporting needs
Compliance isn’t just about checking a box for auditors—it’s about having the right security controls to protect your business. Yet, too many companies overlook compliance features when choosing a SIEM, only to realize later that their system doesn’t generate the needed reports.
If you deal with PCI DSS, HIPAA, GDPR, SOC 2, or ISO 27001, you need automated log retention, pre-built compliance reports, and audit-ready dashboards. Otherwise, you’ll be wasting hours manually generating reports—or worse, paying extra for compliance add-ons you didn’t budget for. The bottom line? If compliance matters to your business, make sure your SIEM supports it natively. Otherwise, you’ll be stuck scrambling when auditors start asking for reports you can’t generate.
Bad SIEM Choice Costs More Than You Think
Avoid misconfigurations, hidden costs, and endless maintenance struggles—get it right from the start.
8 SIEM Buying Criteria That Matter
So how do you cut through the noise and find a SIEM that works? Here are the 8 must-have features to look for—so you don’t waste time or budget on the wrong tool.
1. Real-time threat detection that works
A SIEM shouldn’t just store logs like an expensive filing cabinet—it should actively analyze them in real time, correlate security events, and flag threats before they escalate.
Some tools excel at this. Elastic has strong data analysis and threat detection capabilities, making it a solid choice for organizations prioritizing detailed security insights. Meanwhile, QRadar focuses specifically on security events, which can be a better fit for companies that want a streamlined approach to detection without overwhelming noise.
If your goal is catching real threats, not just collecting endless logs, we suggest you ensure your SIEM has built-in threat intelligence, anomaly detection, and user behavior analytics (UBA) to minimize false positives.
2. Seamless integration with your security stack
No SIEM exists in a vacuum—it needs to play well with the rest of your security infrastructure. If your SIEM can’t integrate with your EDR, firewalls, cloud environments, and compliance tools, you’ll end up spending more time troubleshooting than actually defending your business.
This is where Splunk stands out—with 2,300+ integrations available, it works well for organizations with complex security environments that rely on multiple tools.
If your team doesn’t want to spend months dealing with API headaches, choose a SIEM that connects seamlessly with your existing stack rather than forcing you to build custom workarounds.
3. Scalability—because security needs will grow
A SIEM that works for you today might become a bottleneck tomorrow. As your business grows, log volumes will increase, cloud environments will expand, and security threats will become more sophisticated. If your SIEM can’t scale efficiently, you’ll be stuck with slow processing speeds, outages, or an expensive migration.
Cloud SIEMs are designed for straightforward scaling, supporting auto-scaling and seamless node expansion. If your business expects rapid growth, a SIEM with built-in flexibility will save you from costly reconfigurations and frustrating slowdowns.
4. Compliance reporting that doesn’t give you a headache
If your company needs to meet SOC 2, ISO 27001, HIPAA, PCI DSS, or GDPR compliance, then your SIEM should make reporting easier, not harder.
Many organizations realize too late that their SIEM doesn’t have built-in compliance tools—forcing them to spend hours manually pulling logs or paying extra for compliance add-ons.
QRadar is a strong choice for compliance-driven organizations because it comes with enterprise security monitoring tailored for regulatory frameworks. Our customers often rely on the Splunk App for PCI Compliance, which helps them meet PCI DSS 4.0 requirements without the manual workload.
5. A SIEM dashboard that doesn’t require a PhD to use
Some SIEM dashboards look like they were designed by engineers for other engineers—packed with too much data and not enough clarity. If your team can’t quickly identify threats, investigate incidents, and take action, then even the most advanced SIEM won’t help you.
Splunk provides extended dashboard functionality, offering interactive capabilities and drill-downs for deep investigations. Elastic is highly customizable—great for teams that want complete control over their dashboards but don’t mind a more hands-on setup.
A good SIEM should prioritize clarity, not just data. If your analysts spend more time configuring dashboards than investigating threats, it’s time to reconsider your SIEM choice.
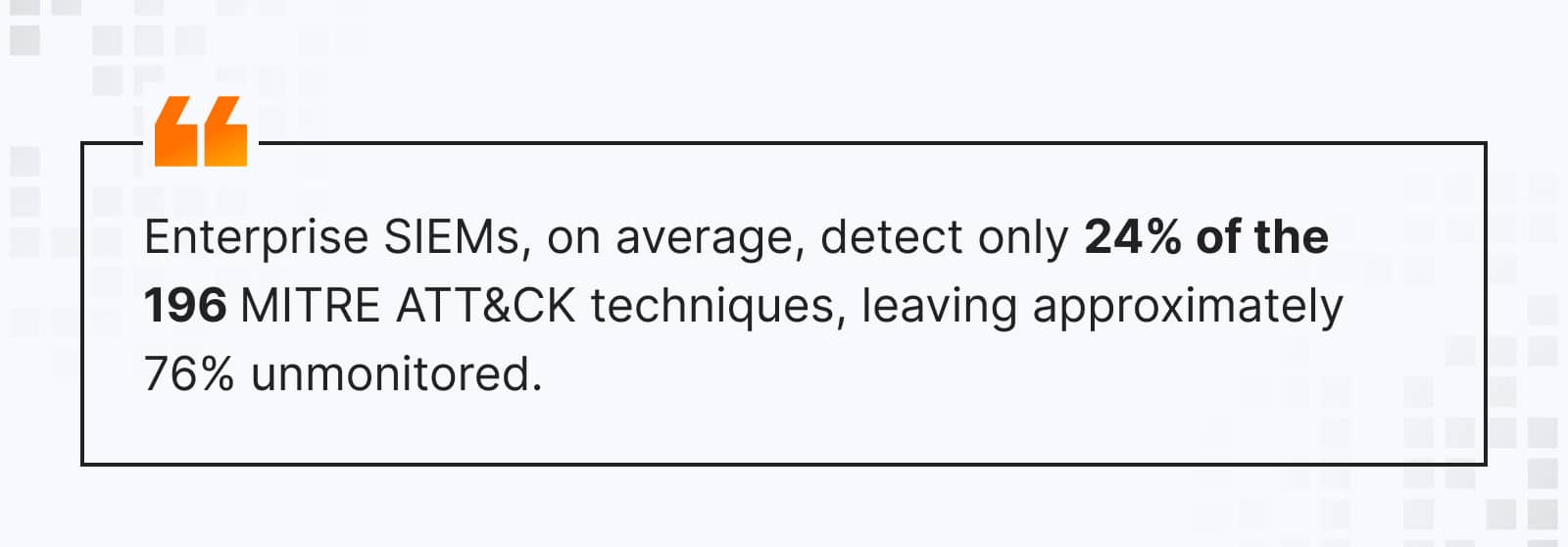
6. SIEM administration & support – DIY vs. Managed SIEM
Managing a SIEM isn’t a side project—it requires constant log tuning, rule management, and full-time monitoring. If your team is already overwhelmed, going the DIY route may not be the best choice.
Most SIEM vendors offer 24/7 customer support — but is it enough? Usually, it’s limited to premium customers—meaning in-house teams still need to handle most of the work. If you don’t have dedicated SIEM engineers, a co-managed or fully managed SIEM solution ensures around-the-clock monitoring and expert response.
The key question: Does your team have the bandwidth and expertise to manage a SIEM full-time, or would a managed service be a better fit?
7. Clear, predictable pricing—no surprises
SIEM pricing is one of the biggest sources of frustration for companies. Some vendors charge extra for log ingestion, additional integrations, or advanced threat detection.
Splunk, for example, has one of the highest initial costs, and its pricing scales based on data volume. That means as your security needs grow, so do your costs. While it’s a great option for large enterprises with dedicated budgets, businesses that need more cost control should consider alternative pricing models. Sumo Logic on the contrary offers low ingest and storage prices, ideal for compliance, but then has a surcharge when using this data for security purposes. SOC teams usually find it complicated to calculate the precise costs for SIEM in such cases.
If you don’t want pricing surprises, make sure you fully understand what’s included in your SIEM’s pricing model—before signing the contract.
8. AI & Automation—because speed matters
When an attack happens, every second counts. If your SIEM can’t automate threat detection, response, and correlation, you’re stuck playing defense instead of stopping threats before they escalate.
Splunk offers advanced machine learning and behavioral profiling, making it a strong choice for companies looking to integrate AI-driven analytics into their security stack. Elastic Cloud also offers AI/ML modules that help catch threats at early stages.
The ability to automate investigation workflows and threat responses can be the difference between a minor incident and a full-scale breach.
SIEM Pricing, Features, & Vendor Comparison—in One Guide
Managed SIEM vs. DIY SIEM
So, you need a SIEM solution—but should you build and manage it yourself or let a Managed SIEM provider handle the heavy lifting? It’s a classic do-it-yourself vs. done-for-you dilemma. Let’s break it down.
Running SIEM logs in-house means you’re on the hook for tuning, troubleshooting, and integrating everything yourself. You’ll need a dedicated SOC team to babysit the alerts, manage the SIEM dashboard, and make sure your logs aren’t just piling up like an unread email inbox. Plus, SIEM integration can get messy fast—especially if you’re juggling multiple security tools that don’t always play nicely together.
On the flip side, Managed SIEM takes all that stress off your plate. Predictable pricing? Check. Expert support? Absolutely. No late-night log analysis marathons? You bet. With a fully managed SIEM solution, you get real-time threat detection, compliance-ready log management, and seamless integration without hiring an army of security analysts.
Here’s a quick comparison between managing SIEM in-house and a managed SIEM provider.
Factor | DIY SIEM | Managed SIEM |
Expertise Required | High – requires in-house analysts & engineers | Low – security experts handle it for you |
Initial SIEM Cost | High upfront costs for setup & licensing | Subscription-based, predictable pricing |
Ongoing Maintenance | Complex – requires rule tuning & log optimization | Fully managed, continuous updates |
Compliance Support | Limited – needs manual configuration | Built-in compliance reporting & support |
Response Time | Slower – internal teams must investigate alerts | 24/7 monitoring & rapid response from experts |
Which one should you choose?
- DIY SIEM – If you love full control, have a rock-solid SOC team, and enjoy SIEM tuning and log analysis as much as your morning coffee, go for it. Just be ready for alert fatigue and unexpected costs.
- Managed SIEM – If you’d rather focus on your business, get expert-backed security, and have real-time log monitoring without operational headaches, this is the way to go.
At the end of the day, security isn’t just about storing SIEM logs—it’s about detecting threats before they wreak havoc. If you want less stress, more security, and a team that sleeps at night, a Managed SIEM solution might be your best bet.
Managed SIEM service models
The great or close to ideal SIEM solution should not only facilitate the swift detection and response to security incidents but also be scalable to go along with future growth, customizable to meet specific needs, and compliant with industry regulations. Furthermore, it should equip your security team with the essential tools to protect your digital assets against any threats and detect any attacks quickly.
As you consider implementing a SIEM solution, you often evaluate different service models to determine which best fits their needs. Here are the primary two types of service models: co-managed and fully managed (or SIEM as a Service).
Below you can find a comprehensive list of services that UnderDefense offers across all SIEM models:
Your SIEM Should Work for You—Not the Other Way Around
Final thought: Don’t gamble with your SIEM investment
Picking the wrong SIEM provider can mean overpaying, drowning in false alerts, or struggling with complex deployments. Instead of guessing, use a structured approach to evaluating SIEM vendors and pricing models.
Not sure where to start? Download our SIEM Buyer’s Guide for a complete breakdown of key features, pricing insights, and vendor selection checklists.
1. What is the primary purpose of a SIEM solution?
2. What are the best SIEM tools available today?
Some of the best SIEM tools include:
- Splunk – Feature-rich, scalable, and widely used in enterprises.
- IBM QRadar – Strong analytics and AI-powered threat detection.
- Elastic Security – Open-source flexibility with powerful log management.
- Microsoft Sentinel – Cloud-native SIEM with built-in AI threat intelligence.
3. What challenges do organizations face when implementing a SIEM?
Organizations often struggle with siloed security data, complex integration, and alert overload. Other challenges include:
- Defining clear security objectives before implementation.
- Managing SIEM log collection across cloud and on-prem environments.
- Ensuring proper SIEM integration with existing security tools.
- Addressing resource and expertise gaps for continuous monitoring.
4. How does SIEM compare to other security solutions like XDR, MDR, and SOAR?
- XDR vs. SIEM – Extended Detection and Response (XDR) provides automated threat detection and response across multiple security layers, while SIEM focuses on log aggregation and analysis. XDR is typically easier to use but may lack the deep forensic capabilities of SIEM.
- MDR vs. SIEM – Managed Detection and Response (MDR) is a fully managed security service that includes SIEM capabilities but also threat hunting, response, and human expertise. SIEM, on its own, requires an in-house SOC team to manage alerts and investigations.
- SIEM vs. SOAR – Security Orchestration, Automation, and Response (SOAR) automates security workflows and responses to incidents, while SIEM focuses on monitoring and logging. Many organizations integrate SIEM with SOAR to enhance security operations and automate responses.
5. How can organizations measure the success of their SIEM implementation?
Success depends on clear objectives and measurable outcomes, such as:
- Faster threat detection and response times.
- Reduced alert fatigue through automation and log correlation.
- Improved compliance reporting for frameworks like SOC 2, ISO 27001, and HIPAA.
- Seamless SIEM integration with existing security tools.
5. What factors should organizations consider when choosing a SIEM provider?
When selecting a SIEM provider, consider:
- Log collection and correlation capabilities.
- Advanced analytics for threat detection.
- Scalability and cloud compatibility.
- SIEM dashboard usability and reporting features.
- Compliance support and integration with security frameworks.













