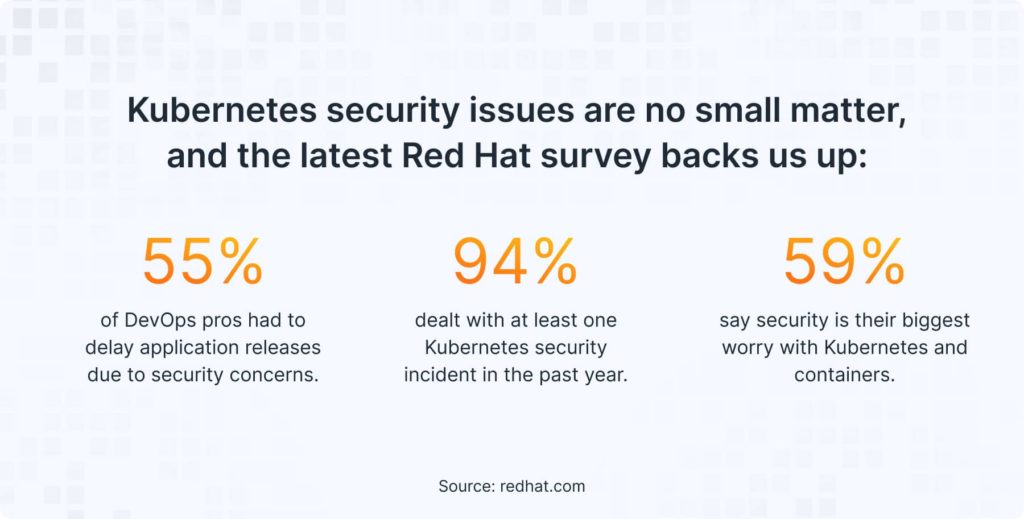
Securing Kubernetes can feel like an uphill battle—it’s dynamic, complex, and a prime target for attackers. Logging failures, unexpected breaches, and lost data can quickly spiral into costly crises, not to mention the recent 2025 compliance demands for full log visibility, which is especially intricate to establish in Kubernetes environments
So, how do you ensure your Kubernetes environment is secure and running smoothly 24/7? I should say, it all starts with implementing the right security practices from Kubernetes monitoring to root cause analysis. Thus, let’s tackle the Kubernetes security best practices to keep your deployment safe, resilient, and compliant.
What is Kubernetes Security?
Kubernetes security (K8s security) is all about keeping your clusters safe from cyber threats. It’s not just one thing—it’s a mix of tools and practices that help you monitor your environment, protect your data, manage access, and stay compliant with security regulations. From containers to workloads, it’s about ensuring every part of your system is locked down and secure.
Kubernetes Security Risks
Even the big guys aren’t immune to Kubernetes risks. Tesla got breached after they didn’t secure their Kubernetes on AWS properly. They have a big security budget but hackers gained access to Tesla’s Kubernetes console, which was left unsecured without a password. Using this flaw, they infiltrated Tesla’s AWS environment and deployed cryptocurrency mining software. This is a reminder that securing Kubernetes is more than just money – it’s about getting the basics right.

Here are the top Kubernetes security risks you need to watch out for:
- Pod-to-Pod networking risks: Kubernetes pods talk to each other for seamless operations, but a breach in one pod can quickly spread to others if network policies aren’t enforced.
- Configuration management: Common misconfigurations include granting too many permissions, using default settings that aren’t security-focused, and allowing root access to containers.
- Software supply chain: Using outdated or insecure components can lead to vulnerabilities easily exploitable by attackers.
- Runtime threats: Without runtime monitoring and detection, attackers can gain control of your infrastructure and exfiltrate data without being detected.
- Infrastructure breach: Breaching a node means an attacker can affect the entire cluster. Thus, you must secure the underlying infrastructure including network and storage systems.
- Compromised images and registries: Make sure your images are built from approved base images, scanned regularly, and stored in trusted registries.
- Lack of visibility: Kubernetes environments can feel like a maze of containers, pods, and nodes, making it impossible to detect vulnerabilities or misconfigurations without complete visibility.
- Unsecured default configurations: Kubernetes doesn’t come with secure settings by default. Secrets management often defaults to storing sensitive data in ways that can be exploited.
- Compliance: Compliance with industry standards like PCI-DSS, HIPAA, or SOC 2 means constant monitoring, logging, and enforcement of security best practices.

11 Kubernetes Security Practices
Securing your Kubernetes deployment is key to keeping your business safe from attacks. Follow this Kubernetes security checklist of security practices to strengthen your cluster.
Let’s meet Jack. He’s the CTO of a fast-growing SaaS company, juggling multiple responsibilities like scaling infrastructure, optimizing performance, and ensuring security—all while keeping the business running smoothly. Jack’s team just migrated their workloads to Kubernetes on AWS, but the more he learns about Kubernetes, the more he realizes the risks that come with it. Security breaches, misconfigurations, and a flood of security alerts have Jack a bit on edge. He knows that getting Kubernetes security right is crucial, but he’s not sure where to start. So, let’s help Jack lock down his Kubernetes cluster with these 11 best practices.
1. Kubernetes Monitoring
Meet Jack’s first challenge: he’s got Kubernetes clusters running 24/7, and without proper monitoring, any security incident could go unnoticed. We tell Jack that continuous security monitoring is non-negotiable. He must spot threats, performance issues, and anomalies the moment they pop up. 24/7 threat detection and prevention or MDR (managed detection and response) solutions can provide comprehensive Kubernetes log monitoring and security management. Security-as-a-service platforms integrate and automate security tasks, while MDR services combine automated tools with expert human analysis to monitor and respond to threats around the clock.
2. Container Security
Jack’s next hurdle? Securing containers. He knows they’re the building blocks of his Kubernetes deployment, but one wrong move could expose vulnerabilities. We suggest he use tools like Clair or Trivy to scan his container images before deploying them. Keeping container images updated and patched is critical. From what we’ve seen, letting a container go unpatched is like leaving your front door unlocked—so Jack makes sure his team follows this best practice.
3. Network Policies
Jack learns quickly that Kubernetes allows free-flowing pod communication by default. This is a huge risk if one pod gets compromised. The solution? Jack implements strict network policies using tools like Calico or Cilium. This ensures only essential pods can communicate, like locking down certain doors in a building. It’s a simple but effective step to contain any potential breaches.
4. Access Control
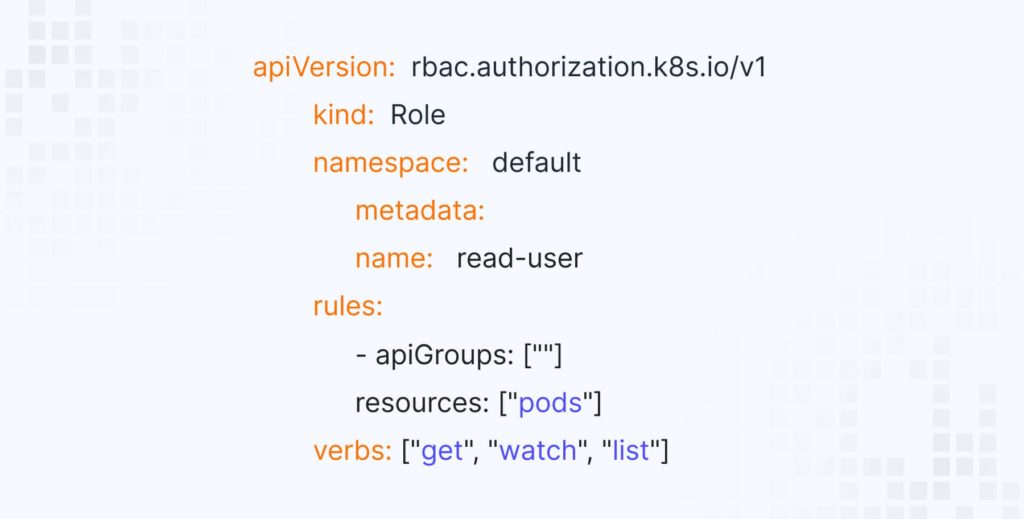
In Jack’s case, access control was chaotic—too many people had too much access. We introduced Role-Based Access Control (RBAC) with the Principle of Least Privilege (PoLP), so everyone only gets the access they truly need. Roles define actions (like reading pod data), and RoleBindings links these roles to users, groups, or service accounts. Jack created a read-user role, which only allows actions like “get,” “watch,” and “list” on all Pods in the default namespace. With this setup, each user has only essential access, keeping Kubernetes secure and streamlined.
Here is what it looks like:
5. Data Encryption
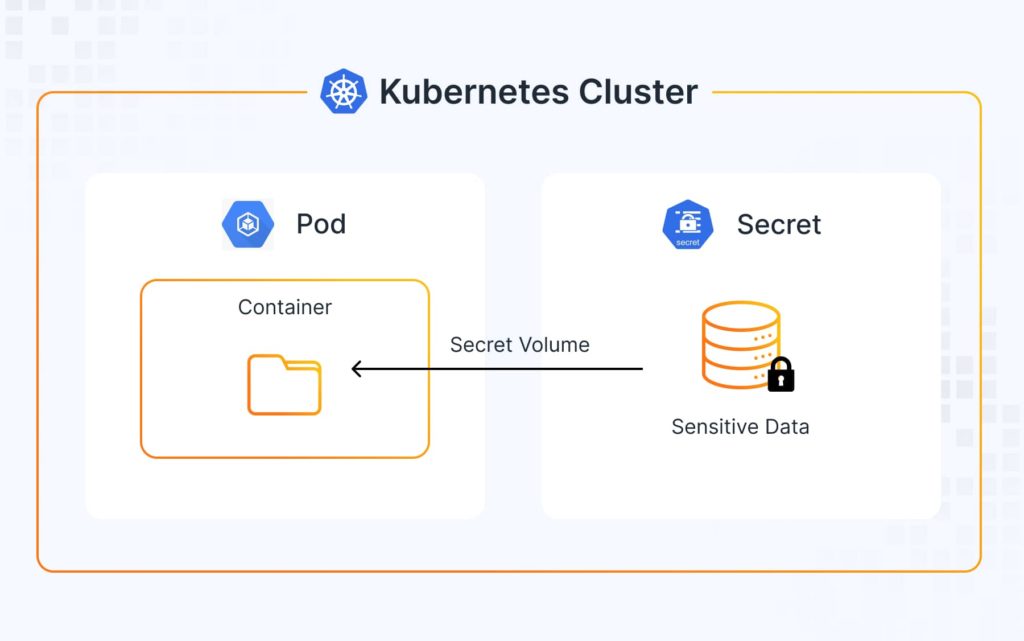
Jack quickly realized that by default, Kubernetes stores Secrets in Base64-encoded format in etcd, which is not secure without encryption. It can be a major vulnerability if an attacker gains access to etcd. We advised Jack to enable encryption at rest for Kubernetes Secrets by configuring the API server’s EncryptionConfiguration. This approach ensures that even if someone accesses etcd, they cannot read sensitive data without the encryption key.
6. API Security
As Jack looks into his Kubernetes setup, he realizes the Kubernetes API is the gatekeeper of his cluster. If the API isn’t secured, it could be game over. We guide Jack through setting up strong authentication and authorization protocols, limiting who and what can access the API server. And of course, audit logging is turned on—it’s like having a security camera at the front door, recording every access attempt.
7. Pod Security
Jack realized his Kubernetes cluster was at risk because pods could potentially have more privileges than necessary. To secure his environment, Jack implemented Pod Security Standards (PSS) to enforce policies like disabling privileged containers and restricting access to sensitive volumes. Additionally, he set up security contexts for each pod, specifying which capabilities are allowed.
8. Regular Updates
Like many CTOs, Jack is busy, but we remind him that updates can’t be skipped. Keeping his Kubernetes control plane and worker nodes up-to-date is crucial for security. Jack sets up automated updates to ensure his systems are always patched and protected. In the tech world, staying up-to-date is like wearing a seatbelt—it might seem like a small thing, but it’s a lifesaver in the long run.
9. Logging and Auditing
We explain to Jack that logging and auditing are his best tools for understanding what’s going on inside his clusters. Tools like ELK Stack or Fluentd gather and process logs, giving him visibility into every move made in his Kubernetes environment. Jack knows now that MDR platforms can centralize all this data, making tracking and responding to potential threats easier. Jack’s team won’t need to stare at logs all day—they’ll get real-time alerts via Slack or Jira if something goes wrong. Automatic alerting helps them focus on what matters while staying on top of their Kubernetes cluster. Moreover, periodic manual reviews are still essential, so security automation platforms are equipped with comprehensive dashboards with reminders to check in regularly, ensuring Jack’s team stays proactive and in control.
10. Runtime Security
Jack’s team has done a lot of work securing Kubernetes configurations, but we tell him that runtime security is just as important. Once the containers run, he needs tools like Falco to monitor for anomalies or malicious activity. It’s like having a security guard on duty while the system is live—catching threats in real time. But Jack soon learned the flood of alerts can be overwhelming. His team was buried in notifications, waking up for false positives. This is where SOC as a Service steps in, offering 24/7 expert monitoring. They handle the noise, cutting down alert fatigue and only notifying Jack about critical threats that need immediate action.
11. Root Cause Analysis
Even with all these protections in place, things can go wrong. When they do, we remind Jack not to just patch up the issue and move on. Root cause analysis is essential for understanding what happened, why it happened, and how to prevent it from happening again. It’s like fixing the leak at the source instead of just mopping up the water.
Kubernetes Monitoring with UnderDefense: Get instant control over your clusters
Kubernetes demands round-the-clock monitoring to stay secure, and the Tesla hack serves as a powerful reminder of what happens when that fails. They had all the budget in the world but missed out on basic security practices—leaving their Kubernetes cluster exposed. A simple, preventable breach allowed hackers to install malware within minutes.
But with UnderDefense MAXI, you don’t have to face these challenges. Let’s break down how it works in just a few steps:
- Seamless integration: Connecting your Kubernetes cluster to UnderDefense MAXI is easy. All you need is your EKS Role ARN, and you’re set. Once integrated, UnderDefense MAXI starts monitoring your Kubernetes clusters in real time, showing up in the “My Tools” tab for instant visibility.
- Immediate incident detection: The moment a malicious file (like a disguised web shell script) lands in your system, UnderDefense MAXI’s File Integrity Monitoring kicks in. An incident is generated instantly. Real-time alerts make sure your team is notified right away, either through a call or email, ensuring nothing slips through the cracks.
- Automated enrichment & AI pre-investigation: UnderDefense MAXI’s automated enrichment playbooks take over, gathering relevant context around the incident. AI helps pre-investigate, providing you with the who, what, and when of the breach. This means you understand the situation right away without the guesswork.
- Security analyst triage & mitigation: A security analyst verifies the data, delivers a verdict, and mitigates the threat by containing and isolating the breach. It’s like having a security expert in your back pocket, ensuring the breach is handled swiftly and properly.
- Future prevention: But it doesn’t end there. After the incident is resolved, your security analyst guides you through how to prevent similar attacks in the future. UnderDefense MAXI also integrates with Jira, so you’ll never miss an important alert, and everything ties smoothly into your workflow.
Learn more by watching our demo video and see how UnderDefense MAXI keeps Kubernetes clusters secure, every minute of every day.
Kubernetes fundamentals: A quick refresh for your cluster Mastery
In case you need a quick refresher, here’s a breakdown of Kubernetes fundamentals to help you brush up on key concepts. Let’s discuss the basics to keep your understanding sharp.

What does Kubernetes do?
Kubernetes orchestrates containerized applications across a cluster of machines, automating deployment, scaling, and management.
Kubernetes security architecture
Kubernetes security architecture involves multiple layers, from network policies and container security to pod controls and access management.
Kubernetes compliance
Kubernetes compliance ensures your cluster meets security and regulatory standards like PCI-DSS, HIPAA, and SOC 2. Regular auditing, data encryption, and access control mechanisms help maintain compliance in dynamic cloud environments.
When should I use Kubernetes?
Use Kubernetes when you need to manage containerized applications at scale with automated deployment, scaling, and operations.
Kubernetes implementation
- Plan your Kubernetes architecture.
- Deploy containers.
- Set up security policies (network, pod, etc.).
- Implement monitoring platforms like UnderDefense MAXI for 24/7 visibility.
- Regularly audit and update your system.
What is Kubernetes used for?
Kubernetes manages containerized applications across a cluster of machines, automating scaling, deployment, and management.
Kubernetes Runtime Security
Ensure runtime security by monitoring container behavior during operation to detect suspicious activity or potential breaches.
Kubernetes Network Security
Implement network policies to control traffic between pods and prevent unauthorized communication or lateral movement.
Kubernetes Image Security
Scan container images for vulnerabilities before deployment and ensure they come from trusted sources to avoid security risks.
Kubernetes Cluster Security
Protect the Kubernetes cluster itself by enforcing security policies, securing the API server, and regularly patching components.
Kubernetes Node Security
Secure nodes by minimizing their attack surface. Disable unnecessary services, apply patches, and use access controls.
Kubernetes API Security
Ensure that the Kubernetes API is secured with proper authentication and authorization to prevent unauthorized access.
Kubernetes Pod Security
Set pod security policies to control how pods are deployed and managed, preventing insecure configurations.
Kubernetes Data Security
Encrypt data at rest and in transit to safeguard sensitive information in your Kubernetes cluster.
Kubernetes Namespace Security
Isolate sensitive workloads using namespaces, ensuring proper access control and reducing the risk of cross-namespace attacks.













