Customer view:
Guest blog by Michael Rezek, VP, Cybersecurity Strategy at Accedian
It may be possible to spend less on cybersecurity and get more protection
What we have witnessed over the last couple of decades as the traditional approach to corporate Cyber Resiliency has been a focus on attaining certain levels of maturity by building certain capabilities into the cybersecurity program. To achieve “maturity”, an organization might build a SOC to improve how they assess, monitor, and respond as well as implement other capabilities such as multi-factor authentication to reduce access control risk. This might be referred to as a maturity-based approach to cybersecurity which can be helpful as an initial step in building cyber resiliency into a business in its infancy, as every business needs to start somewhere. However, a maturity-based approach is insufficient to address today’s sophisticated and unrelenting cyber-attacks for businesses that have the basic building blocks in place.
One of the challenges is that maturity-based approaches tend to grow out of control as they seek to “protect everything 100%”. The fact is that in today’s hyperconnected world, maturity-based Cyber Resiliency programs are no longer effective to address cyber-risks. Also, implementing controls with a goal of “100% protection” can stifle innovation, business agility and create project gridlock. Most often, just increasing spend alone on controls is not going to reduce risk beyond a certain point (see graph below).
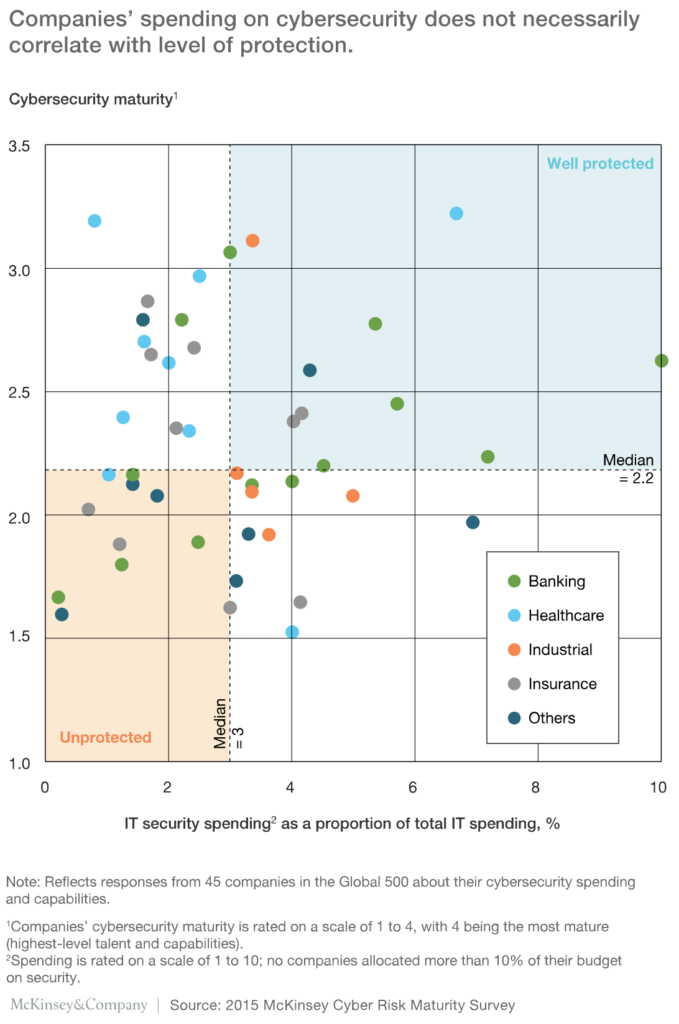
The most sophisticated businesses nowadays are adopting what is called a risk-based approach to Cyber Resiliency as organizations need to transition to focusing directly on risk reduction. As an example, they should move from a position of monitoring every application to the ones that pose the greatest risk to Business Continuity should they be compromised. Other benefits to risk-based Cyber Resiliency are that allocation of spend can be prioritized on the highest risk and that Cyber Resiliency targets can be aligned and measured against senior management’s and board risk-reduction targets. With a risk-based approach, a company will no longer “build the control everywhere”; rather, the focus will be on proportionally implementing control and investment to risks that pose the greatest danger to business continuity. More often than not, greater risk reduction can be realized by investing in places such as proactive ethical hacking and employee awareness and training than just increasing spending on tools and technology to acquire the ever-elusive 100% protection.

UnderDefense’s Cyber Resiliency Advisory and Consulting services can help you understand where your vulnerabilities are across your organizations’ people, processes and technology as well as understand relevant threat actor capability and intentions that could threaten your Business Continuity. UnderDefense’s elite Ethical Hacking teams defeat industry recognized tools, technology and MDR services daily. How do you know if your investments in these areas are resilient or can be defeated and that the risk reduction investments you are making are actually successful in providing their intended return? One way is to hire a team of elite ethical hackers to identify gaps and areas of over-investment that are disproportionate to the respective risk. UnderDefense can also stress test your risk assumptions as consultants as well as pragmatically with their elite ethical hacking service.
This is where spend can often be recaptured and be redeployed into areas that need it and over time even be reduced. This adaptive and sustainable risk management approach is essential in today’s digital business era given the dynamic nature of business practices, partners, suppliers, customers and architectures via digital transformation and the move to cloud and multi-cloud infrastructure. Given this dynamic nature of digital business and today’s cyber threats, the assessment of risk and balancing risk severity with appropriate spend, is a continuous process and most often requires an advisory ally like UnderDefense. When a cyber-attack creates chaos, you want the most elite force on your side. …BUT WHAT IF that same elite force could prepare you in advance to fortify your Cyber Resiliency by adapting cybersecurity spend according to risk to prevent the inevitable loss of Business Continuity following a cyber breach? Reach out to UnderDefense to learn more.


















