The statistics show that cybersecurity issues are becoming a day-to-day struggle for businesses. That’s why thinking about your security posture is a number one task for all go-ahead companies. Your sensitive data and money won’t be vulnerable if you have proper business protection to cyber threats in place. In case you have mismanaged, unorganized, and insecure data, an attacker from outside or inside may use it as your weak point.
Protecting your business, your customers, your data, your viability, and your integrity from cyber threats is the right strategy to follow. To do this you should build a security plan which leads you to mitigating all pains and building layered security. The cybersecurity portfolio provides you with different solutions to situations as each case requires a unique approach. Without professional help you may not know which service you need at the current stage. Our security roadmap shows resolutions for your pains and moves you step by step closer to the safety and wellness zone:
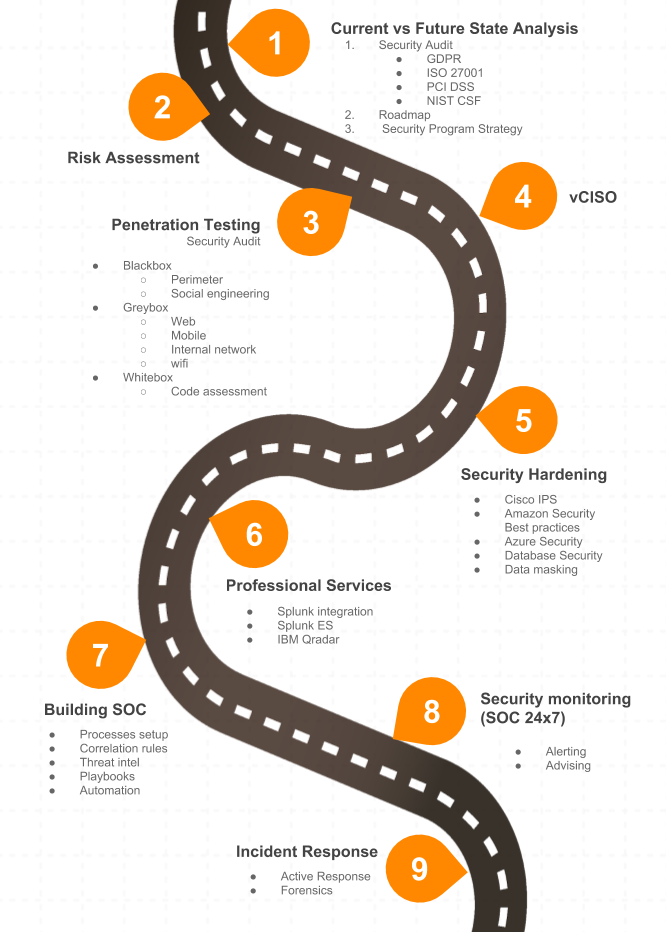
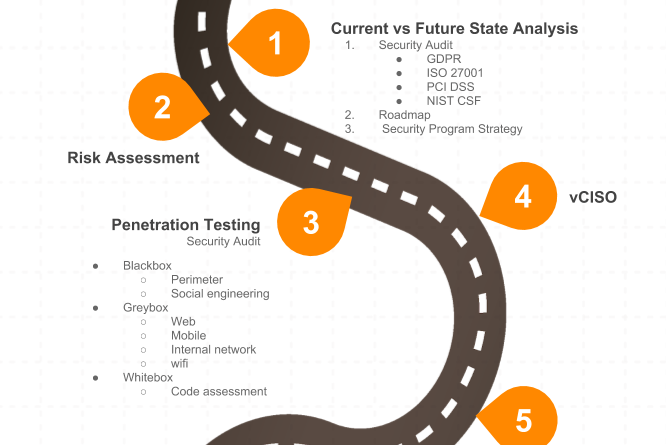
- Current vs. Future State Analysis – is usually the first point of learning about your safety condition. At this stage you get screening of your security posture in case you prepare for certifications and compliances ( GDPR, HIPAA, PCI DSS, ISO 27001, SOC1, SOC2). Other cases are if you want to get the current view of your security, know where to move further with uncovered gaps, or receive insights from security experts how to develop your internal protection strategy.
- Risk assessment – is a service that you need if you want to evaluate the potentials risks in a particular environment and also get plan for future with areas you should strengthen.
- Penetration testing/ Security audit – takes a look at your security perimeter from the view of a “bad guy”. The pentester tries to get the access to the system in a role of an attacker or acts as an insider threat. This could be your angry fired worker or a thief that does fraud actions undercover. Penetration testing detects flaws in your system to catch out pitfalls before the hacker does it. To test your system different ways are used. We do all kinds of pentests. Learn more here.
- vCISO – if you need to set up all security processes in your company, a dedicated virtual Chief Information Security Officer does this for you. He can interact with your existing security team or IT team by monitoring, checking and supporting your IT environment.
- Security Hardening – is the process of strengthening your state of security by implementing best security practices. If there is a product that you bought in past, but don’t know how to use it, we can help you to deploy and configure it. We do Cisco IPS, AWS best practices, Azure Security, Database security or data masking and many others.
- Professional services – include deployment, building the architecture, PoC, implementation and support of different solutions that you have in-house. If you have a tool, but lack the resources to integrate it, UnderDefense team will help in all previously mentioned cases. Currently we work with such SIEM tools as Splunk, Qradar and Mc Affee.
- Security Operationals Center building – usually it’s a challenge not only to find good security analysts, but also to train them on real use-cases and raise their expertice. We can share our knowledge how to grow them up into a solid SOC and teach them detect and react to threats.
- SOC monitoring – unfortunately, building your own SOC demands lots of money and resources. A wise solution to this issue will be outsourcing SOC services. Monitoring logs in your environment is a high-level protection not only to prevent threats, but also to respond to them fast. It can works in different modes: fully managed or co-managed. Depending on your business size and the amount of logs processed, we adjust to your needs and help you to have the over-clock presence and keep an eye on your business 24/7.
- Incident Response – is a separate service or a part of our SOC service. Responding fast to the breaches and incidents is possible when you have Incident Response playbooks in place. We help you get ready even to the most unpleasant moments and report or recover from a breach or cyber attack.
Our last but not least service launch is the SecOps AWS training were we give you hands-on experience how to implement best cloud practices. All the time we expend our qualifications and knowledge to help you feel secure and protected. Contact us directly to get more information projects we’ve completed or view our clients feedback here.