News about severe security breaches is becoming commonplace. As the former FBI Director Robert Mueller said “It’s not a matter of if, it’s a matter of when.”
Consumers are bewildered about how this keeps happening.
Is anyone genuinely safe nowadays?
Every organization should take data security very seriously. After all, a data breach can cost the business millions of dollars and undermine its credibility and reputation.

Generally, cybersecurity is focused on protecting and securing some assets and their interaction. Preventing data breaches is the best defense against the nightmare and expense that comes with them. Before you can stop a data breach, you must understand them, though. The types and costs of data breaches you might experience as a small- to medium-sized business owner are described below, along with tips on how to avoid them.
Table of content
- What is a Data Breach?
- Who is typically targeted for data breaches?
- Causes of Data Breach
- Which are the biggest data breaches?
- What should I consider when my data is breached and stolen?
- Ways to Prevent Data Breaches
- How UnderDefense Can Help you prevent Data Breaches
What is a Data Breach?
A data breach is a security incident in which sensitive and confidential information is extracted from a system by an unauthorized individual, group, or software system, without the owner’s knowledge or consent. A data breach involves some kind of penetration and consequently different manipulations of data, e.g. using, publishing, or blocking the breached data so that the data owner cannot use it or rely on it.
Who is typically targeted for data breaches?
Anyone can be hacked or targeted for data breaches. It`s just a matter of time and effort. So hardly any business, small, medium, or large can be genuinely safe.
However, some areas can potentially be attacked to gain access to their sensitive information. Financial, health, intellectual, and government information is most likely to be stolen, which determines the industries most vulnerable to data breaches.
Although there is some debate over the order, the top industries that are most exposed to cyberattacks are as follows:
- Business/Retail
- Government/Military/Public Administration
- Medical/Healthcare
- Finance/Insurance/Banking
- Education/Research
- Energy/Utilities
But we must bear in mind that other industries also face similar risks of inside or outside attackers breaching their important data.
Causes of Data Breach
It’s critical to comprehend the most frequent reasons for data breaches and what you can do to lessen the risks the data breaches pose if you intend to keep your own company out of the headlines.
1.Human Factor
- Weak and compromised Credentials (passwords)
- Sharing sensitive information with the wrong recipients
- Falling for phishing scams etc.
- Violation of the organization’s policies and security controls
2.Insider Threats (deliberate abuse of the company’s systems by an authorized user)
3.Legacy, Unpatched Application Security Vulnerabilities, Improper Configuration
4.Malware (malicious software)
5.Social Engineering
6.Improper access management
7.Physical Theft of a Data-Carrying Device
8.Improper treatment of data security risks
Which are the biggest data breaches?
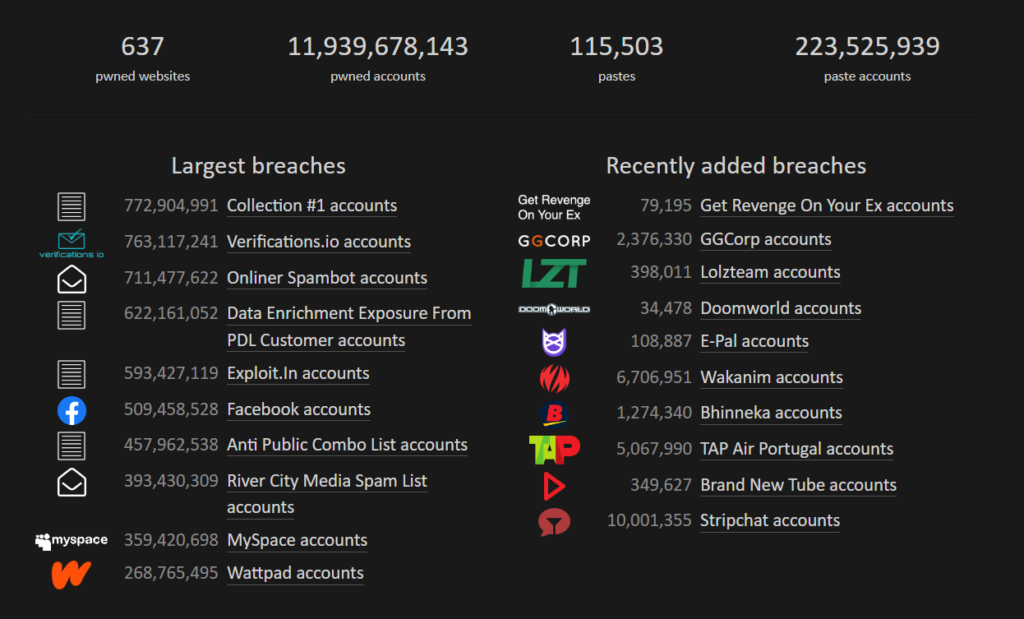
Data breaches occur regularly leading to irreversible consequences. Among the most significant data breaches are the Yahoo data breach (2013), the Facebook data breach (2019), the LinkedIn data breach (2012), the Adobe data breach (2013), Microsoft Data Breach (2022), Red Cross Data Breach (2022), etc. This list of data breaches goes on and on. A staggering 3 billion records were exposed in the greatest data breach in history. And it is estimated that data breach attacks cause annual global losses of trillions of dollars. Analyzing previous data breaches can teach us many valuable insights. In reality, if businesses had adhered to basic cybersecurity hygiene best practices, several of the most serious data breaches would have been avoided.
Where does Data Protection Begin?
What should I consider when my data is breached?

The term “data breach” sounds threatening but it is ambiguous and a bit of a buzzword. Not everyone who talks about or anticipates data breaches actually realizes what exactly can be breached.
The first question we need to answer when thinking about data breaches is what kind of data should be protected. To understand this, we must identify, classify, and prioritize the data first.
When it comes to information security, both cyber and physical security are typically taken into account. Most people will consider items like laptops and servers when we discuss assets. We regard anything valuable to the company to be an asset. A device, a piece of data or information, a software application, a cloud service, or even an individual can also be an asset. Depending on the type of asset storing data we may need a different approach and different data breach prevention measures.
When we see the big picture and understand how assets and data are correlated and combined, it will allow us in the future to adequately address the issues and take necessary measures to prevent data breaches.
Information Security Strategy development is another significant step in preventing data breaches. If you have a clear understanding of the types of assets you own and their criticality, it is much easier to build a safety control implementation strategy tailored specially to your business needs.
Who can build the Information Security Strategy? It might be a security expert working for the company or you can hire a vCISO to help you.
The strategy requires time and an allocated budget and is split into some steps it should always be approved by a company CIO/CEO. These steps actually may involve making a tactical decision.
Steps to Prevent Data Breaches

An answer to the question of how to prevent a data breach could be different, depending on the person. Company managers or technical experts will most likely give differing responses. However, there are essential steps to be taken if you are willing to secure your data from being breached.
1. Hire a cybersecurity expert.
If your organization lacks a competent resource, consider hiring a cybersecurity professional.
2.Develop a cyber breach response plan and data backup and recovery plan.
Integrate and Test it to ensure that it functions as well as anticipated and that individuals are trained enough to know what to do.
3.Third-party vendors must comply.
Giving third-party providers access to your systems opens up new entry points for cybercriminals trying to break into your network. You should confirm that your suppliers are just as serious about cybersecurity as you are. Potential weaknesses must be addressed and, if necessary, mitigated. Cyber risk analyses will assist you in determining the security measures your vendors already use and how resilient they are to attacks and data breaches.
4.Security Awareness training is a process of formally educating a workforce about the numerous cyber threats that exist, how to recognize them, and precautions to take to keep businesses secure.
Usually, it is regarded as a long-term plan and a component of a bigger security program. The advantages of security awareness training are extensive:
- Employees will become more cyber-aware and have the knowledge and confidence to identify security threats when they are present as well as how to respond appropriately and escalate the issue with the help of a strong security awareness training program.
- When it comes to commonly used applications and technologies at work, such as social media, email, and websites, employees will be aware of information security best practices. Employees that have received security awareness training are better informed about common social engineering threats like phishing and spear phishing.
- By implementing a security awareness training program, you can increase your company’s security and support your compliance efforts by ensuring that your staff are aware of compliance guidelines and know how to handle sensitive data and information.
- Customers will be more willing to do business with you if they see that you’re being more proactive with your cybersecurity procedures and that security awareness training is one of your company’s available resources.
5.Secure endpoints and mobile devices.
To begin with, you can use EDR (a group of tools known as endpoint detection and response, used to identify and look into endpoint threats and typically offering capabilities for threat hunting, threat detection, investigation, and response) and MDM (Mobile Device Management through which IT administrators can safely monitor and manage mobile devices that access confidential company data, it allows keeping track of important information about mobile devices, selecting which apps can be installed, locating devices, and safeguarding devices in case they are stolen or lost).
6.Patch and update the software as soon as options are available.
Upgrade devices when the software is no longer supported by the manufacturer. You might need the plan to keep track of EOL and include additional expenses in your annual budget. To be always aware if some software is outdated consider using a vulnerability scanner or other soft giving you the possibility to monitor the assets.
7.Secure Network Perimeter using next-gen firewalls and zero-trust principles.
Zero Trust is a security framework that mandates that before granting or maintaining access to applications and data, all users—whether inside or outside the organization’s network—must first authenticate, authorize, and undergo existing security configuration and posture validation. Zero Trust is based on the premise that there is no such thing as a traditional network edge and that networks can be local, in the cloud, hybrid, or a combination of both, with people and resources spread around the globe.
Like software-defined perimeters (SDP), ZTNA (Zero Trust Network Access) leverages the concept of a dark cloud, preventing users from seeing any applications and services that they don’t have permission to access. This introduces protection against lateral attacker movement, where a compromised endpoint or credentials would otherwise permit scanning and pivoting to other services.
8.Monitor the infrastructure using advanced security tools.
Artificial intelligence is used at many levels in advanced cyber security technologies like EDRs and SIEMs (Security, Information, and Event Management) to find and notify about indications of intrusion. To identify and react to indications of malicious software or activity, an EDR tool operates at the endpoint level. Similar work is done by a SIEM at the level of your entire network, which scans records and traffic for potentially dangerous behavior.
Many EDR and SIEM technologies go beyond AI and automation to offer a team of IT security specialists to evaluate activities identified by the software and assess whether the authorities (a company’s IT department or MSP) should be contacted. To detect and respond to harmful activity on endpoints or the network, they combine machine and human intelligence.
9.Limit access to your most valuable data. Keep only what you need. Encrypt data.
Consider the Principle of Least Privilege according to which a subject should only be granted the privileges necessary for them to carry out their work. A subject shouldn’t be granted an access right if they don’t require it. Furthermore, the assignment of rights ought to be governed by the function of the subject rather than its identity. When an activity is finished, all further access permissions that were granted to a subject as a result of that action should be withdrawn. According to this principle, processes must be contained inside a minimal amount of the protective domain.
Also, there are software solutions providing different access control models configuration. The set of regulations and tools known as Access Control determine which resources authenticated users are allowed to access. Depending on their security needs, infrastructure, and other factors companies select one of the four most popular access control models:
- Mandatory Access Control (MAC)
- Discretionary Access Control (DAC)
- Role-Based Access Control (RBAC)
- Privileged Access Management (PAM)
10.Analyze the Risk and Establish Security Policies.
When your company is ready to operate with Business Risk, we highly recommend adding Cybersecurity Risks to your table to help your business strategy protect valuable data. For example, you may not need Vulnerability Management at the moment because you have only a few endpoints, so the Risk of attack is Low because it does not require a lot of effort to install patches. However, your Organization can grow with your endpoint assets, so the Risk can become higher as well. At this point, you should implement Vulnerability Management.
However, keep in mind that even in a small business vulnerabilities can be found, so in fact, you should have a vulnerability management process, of course, if you have 5 laptops you can perform the reviews manually and probably you will have a plan on how to mitigate incidents in your head and do it right away, but even this is a kind of vulnerability management process, and if you consider documenting it somewhere it will metamorphose in a Vulnerability Management Procedure.
11.Other tips that may increase your Data Protection:
- Enforce strong credentials (passwords). Encouraging users to start using a password manager can help. Use multi-factor authentication to encourage better user cybersecurity practices.
- High-grade encryption for sensitive data.
- Use secure URLs such as HTTPS (HTTP over TLS) instead HTTP.
- Protect portable devices. Safeguard physical data. Destroy data before disposal.
- And a lot more
How UnderDefense Can Help You Prevent Data Breaches
Combining the appropriate technologies, techniques, and expertise to patch security holes results in a robust cybersecurity posture, and both state and private companies really ought to give security enough consideration to prevent irreversible damage caused by data breaches.
Your customer data and financial information are safely maintained within UnderDefense’s solution, which relieves your company of some of the accountability and risk. To safeguard your company and the clients you serve, UnderDefense makes use of the most sophisticated security and encryption techniques currently available. Organizations can fully control and see everything linked to their network owing to UnderDefense.
Our Managed Detection and Response (MDR) is an advanced 24/7 security control that performs threat hunting, monitoring, and response using a combination of technology and human skill. The primary advantage of MDR is that it quickly identifies and reduces the impact of threats on organizations that cannot maintain their own security operations center.
Organizations that want to do regular security audits of their product or infrastructure and adhere to security requirements will benefit from Penetration Testing.
To learn more about our solution and security measures, contact our team today!

















