Remote IT Security Officer
Delegate doing routine Information Security operations and build solid cybersecurity program with the help of the remote IT security officer. We have your back in making you compliant
Remote IT security officer or virtual Chief Information Security Officer (vCISO) is a dedicated security point of contacts for all issues that helps to build a customized security roadmap no matter where you are on the journey now.
Rapidly growing businesses may not have a complete security program, full-time CISO, and in-house resources with deep insights and knowledge on how secure operations should be developed, implemented, run, and managed. We recommend your virtual CISO solution. With CISO as a service (our expert as a part of your team), your organization will develop a tailored cybersecurity program aligning your business goals and technical needs that fit your profile and get you compliant.
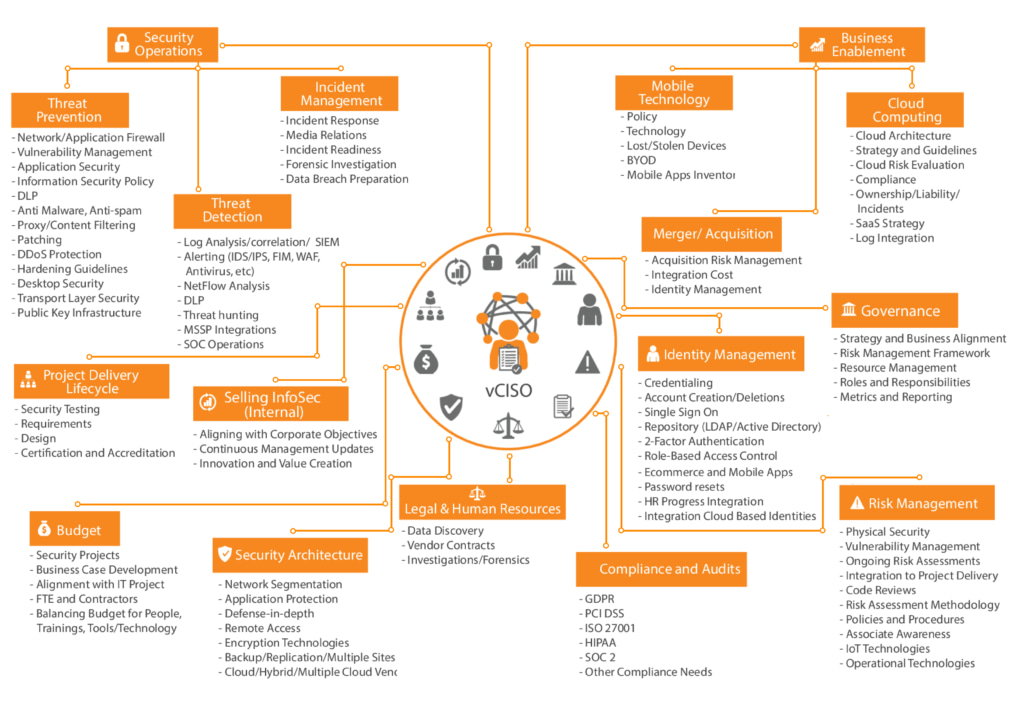
Virtual CISO services overview
Virtual CISO program benefits:
- Meet PCI DSS, SOC2 Type I & II, HIPAA, GDPR, CCPA, NY SHIELD Act compliance
- Ramp up a secure product
- Set up secure operations processes
- Reach cost economy with secure SDLC process
- Protect from Social Engineering Attacks
- Establish Incident Response processes
Virtual CISO objectives:
- Strategize, plan and execute security strategy (customed RoadMap) that aligns with your business goals
- Continuously set up, maintain and enhance controls and processes
- Establish security Leadership in the company
- Set up security Education program with perpetual social engineering checks
- Develop Incident Response security program
Virtual CISO program scope:
- The project duration can be on-going and on-demand. It covers:
- Security Assessment
- Security Operations Development
- Security Talent Allocation/Training
- Threat modeling
Virtual CISO
duties:
- Information security program leadership
- Security Point-of-Contact for All Issues
- Building security Strategy & Roadmap
- High-level cost estimates for budgetary purposes
- Project planning and execution
- Testing implemented policies and procedures
- Guidelines & Best Practices
- Communication with Top management
vCISO security program steps
1
Security Assessment
2
Security Operations Development
3
Security Talent Allocation/Training
4
Threat Modeling
Starting with a Security Assessment virtual CISO team is able to define all the critical areas of an organization that needs to be improved. Engaging with your company, dedicated security experts of CISO services will make up a customized plan on how to find all gaps and put them into calendar remediation processes, helping you save on budget by filling gaps found within your existing staff.
Once the gaps have been exposed, our team of security experts from vCISO services works with you to resolve these issues through a process of product and strategy recommendations, compliance, and regulatory guidance. The experts of vCISO security services support strategic business objectives, alliance with existing policies and processes, and/or the technical requirements of your existing IT infrastructure.
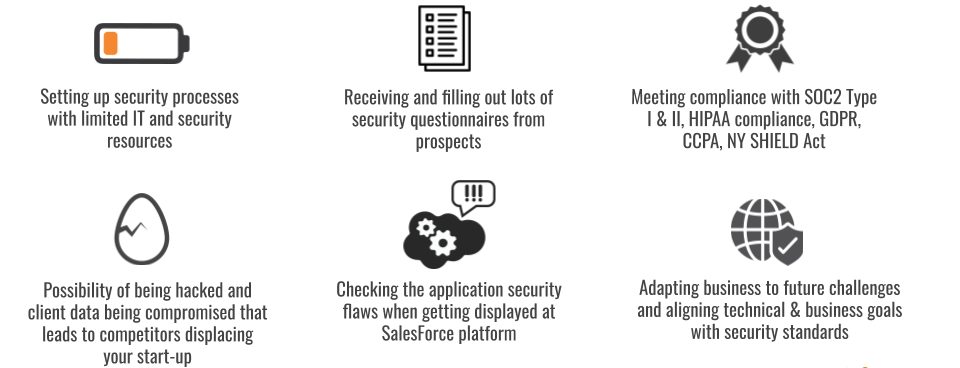
Why you need it?
FAQ
What will our Virtual CISO do for you?
– Information security leadership
– Guidelines & Best Practices
– Governance and Compliance
– Security Point-of-Contact for All Issues
– Steering committee leadership or participation (engaging the client/management/board)
– Security policy, process, and procedure development
– Incident response planning
– Security training and awareness
– Planning Security assessment
– Planning Penetration testing
– Planning Social engineering
– Analyze results of Vulnerability assessments
– Risk assessment
– Conduct initial planning, such as establishing timelines, document scope and confirming your objectives
– Conduct an initial IT security audit and Gap analysis
– Determining level of acceptable risk, identifying critical assets
– Aligning your business strategy with IT security policies
– Conduct regular and thorough information gathering sessions
– Define and develop key IT security policy components
– Remote Access policies and process
– Third-Party security controls
– Security operations processes
– Identity & Access Management
– Personnel Security and Training
– Security architecture and design
The deliverables for the virtual CISO services:
– Presentation of the recommended security strategy & roadmap
– A chronological roadmap depicting projects and priority
– High level cost estimates for budgetary purposes
– Answers to any and all questions to ensure successful knowledge transfer
– Communicating business risks, threat scenarios and estimating impact for critical security events with top management
– Documentation discussing identified projects outlining why they are important, and possible consequences if they are not executed
– Assistance with putting a plan on the company’s calendar
– Project planning and execution, identifying suitable third party support and setting up requirements for a successful completion
– Testing implemented policies and procedures actively through practicing them within the organization and continuously optimizing efficiency
– Developing metrics for the organization to evaluate improvements and security progress throughout time
– Conducting security awareness testing and training programs and running continuous assessments to identify weakest links within the organization
Related Resources
Get Started with UnderDefense
Discuss your project and scope with our experts and start your journey to better, more secure future now









