Respond to the Unexpected with Confidence
Let's TalkStay one step ahead of hackers. Always.
Faster mean time to respond compared to the industry average
Of manual incident response processes can be automated
On average to onboard UnderDefense for security incident response services and enjoy the fastest time to value
Respond to incidents 24/7 while reducing cost and risk exposure
Excellent and cost-effective IR service
24/7 threat hunting and response
Reliable evidence acquisition & reporting
The broadest decryption support & speed
Benefit from the broadest coverage of cybersecurity incident response services
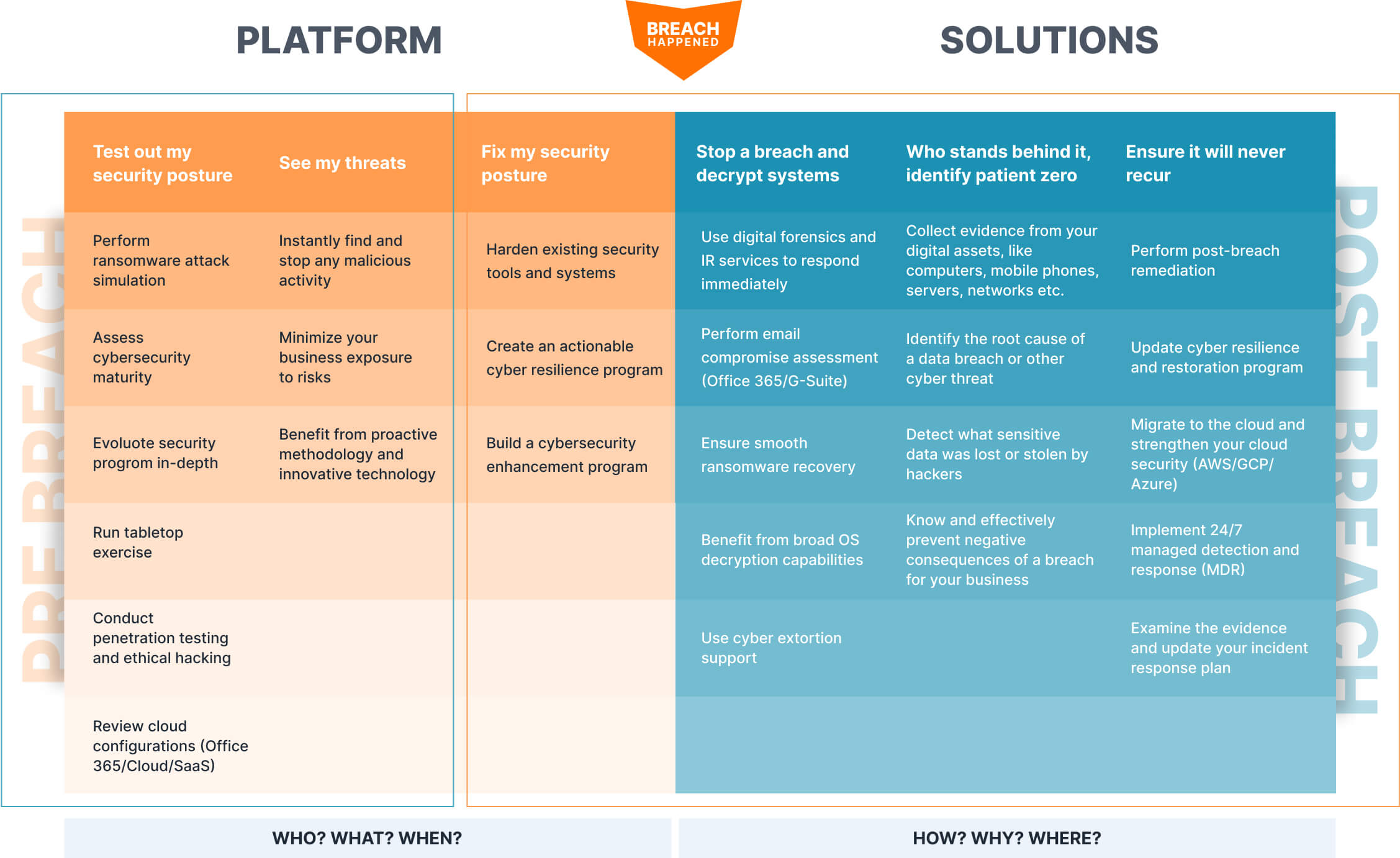
Expand your IR capabilities to stop active security breaches across your environment anytime
Managed security services:
incident response kickoff
Not sure where to begin?
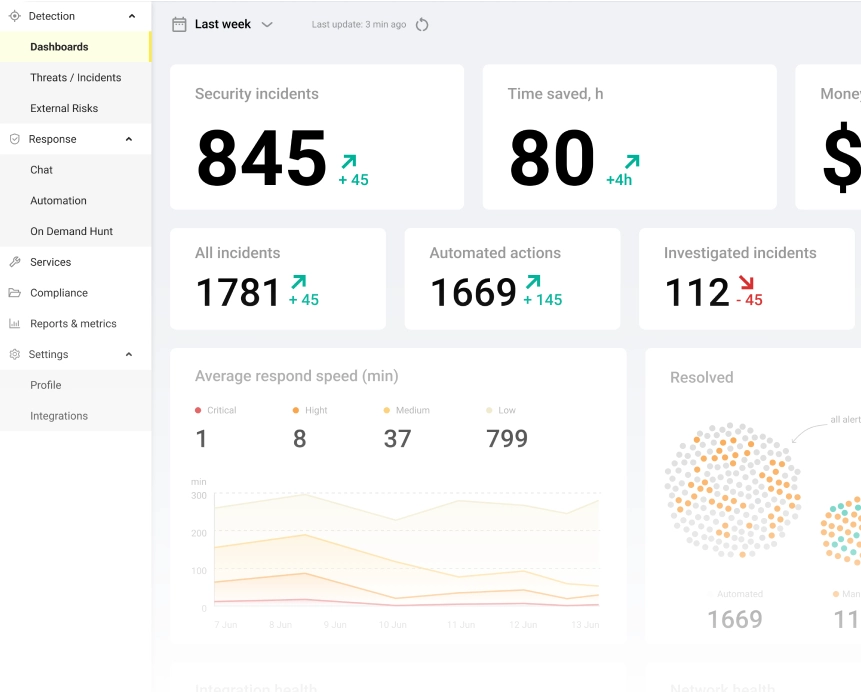
Start by analyzing your current security posture and proactively hunting for threats using the UnderDefense MAXI platform.
Register for free to tap into innovative security technologies, minimize your business exposure to risks, and get expert support whenever you need it.
Why 500+ companies
have chosen UnderDefense
“Immediate value. Very professional approach.
Fast, efficient, and easy to work with."
— These are just a few phrases business leaders use to describe their experience with UnderDefense.
Read more stories from our customers and find out why organizations call UnderDefense mission-critical to their cyber protection.
Best CyberSecurity Provider 2022
on Clutch
Splunk Boss of the SOC 2023
out of 182 teams
Average rating on Gartner Peer Insights for MDR Services
Our awards and certifications



Frequently asked questions
What does an incident response team do?
An incident response team is a group of specialists who prepare a business for emergencies and help it react to them properly. Their areas of responsibility may vary from company to company; however, in most cases, an IR team takes on end-to-end incident response services, including the following:
- Response to all types of security incidents, like attacks, data breaches, or system failure
- Creation of proactive and reactive incident response plans
- Support of all types of incident-handling activities
- Maintenance of solid security best practices and procedures
What is an incident response plan?
An IR plan is a trustworthy and comprehensive roadmap that directs business stakeholders from threat detection, triage, and investigation to containment and eradication. This go-to documentation kit covers the following:
- What threats and situations must be considered security incidents, and what staff must do when they happen
- Who is responsible for performing certain tasks in case of a security incident, and how employees can reach them
- When specific tasks must be performed by the staff
- How exactly staff must complete those particular tasks
Why do you need an incident response plan?
What are the key cyber incident response steps?
- Preparation. Create an exhaustive list of all your assets and endpoints with a defined importance score. Ensure you have monitoring tools in place to understand your normal activity, assess behavior patterns, and collect other metrics to see when something unusual happens. Decide what security events should be blocked and investigated immediately.
- Detection and incident analysis. It all starts with collecting data from all your existing security tools, IT systems, public resources, and more. Then goes the analysis stage, where the normal and current activity of the affected system is assessed. Security specialists need to correlate related events and understand how they differ. It may be the most complicated and time-consuming step because it requires constant switching between contexts and interfaces and manual correlation and analysis.
With UnderDefense MAXI, you can make this process easy and fast. The platform provides all the key features and capabilities for smooth and effective monitoring, risk detection, and analysis of security incidents. - Containment, eradication, and recovery. Blocking a threat before it incurs losses is one of the most important goals of incident response managed services. The containment procedure will vary depending on the severity, potential damage level, the need for vital systems' availability, and more. During the next stages, eradication and recovery, you may need to clean the environment, remove all incident elements, restore systems, or reset account details depending on the type of attack and affected assets.
- Post-incident. Use the lessons learned to improve your security processes, IR plan, and corporate policies and procedures after each incident.
What is the key to effective incident response?
Things to check out
Penetration Testing Report: Free Template and Guide
Do you need a pentest but are worried about deciphering the report? Are you seeking a pentest...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Despite Azure's impressive features, it's important to note that it's still susceptible to...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Detecting Invisible: passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems…