Healthcare institutions, large and small, have always been prime target for cybercrime. Lately, healthcare is transitioning from its traditional focus on disease, accidents, etc., toward the prevention and management of chronic conditions.
This means that the healthcare industry uses a broader ecosystem to deliver a more personalized approach to consumers, enhance productivity, engage caregivers, and improve outcomes and affordability. Given that healthcare has lagged other industries in productivity, it is turning to technology as never before to support practices such as self and autonomous care and to reduce complexity and cost between supporting healthcare providers and stakeholders.
Making the healthcare ecosystem much bigger than ever before, everyone in the chain must be cautious as cyberattacks are of particular concern for the healthcare sector because attacks can directly threaten not just the cybersecurity in healthcare systems’ and information (like electronic health records) but also the health care delivery, personal health, and safety of patients.
Industry numbers:

The rise of the healthcare ecosystem drives healthcare technology convergence
The rise of the healthcare ecosystem drives healthcare technology convergence
Healthcare ecosystems rise and become more effective. Centering around the patient, they provide benefits such as addressing industry inefficiencies, optimizing underutilized assets/resources, eliminating friction in consumer experience, creating stickiness by providing structural advantages, network effect benefits as they grow and create more value for suppliers, and use the data generated in the ecosystem to tailor solutions for suppliers and consumers.
This last point, sharing data, requires platform and API integration which is taking place at a once in a generation accelerated rate across clouds and over private and public networks, or technology convergence. Players in this emerging ecosystem include outside of traditional healthcare and insurance providers include Biopharma, home care providers including remote monitoring services, social care providers, fitness, nutrition and activity providers, financial providers, etc. all with interest in the patient’s wellness, and all providing data back into the ecosystem.
Healthcare ecosystems might be divided into infrastructure, intelligence, and engagement layers.
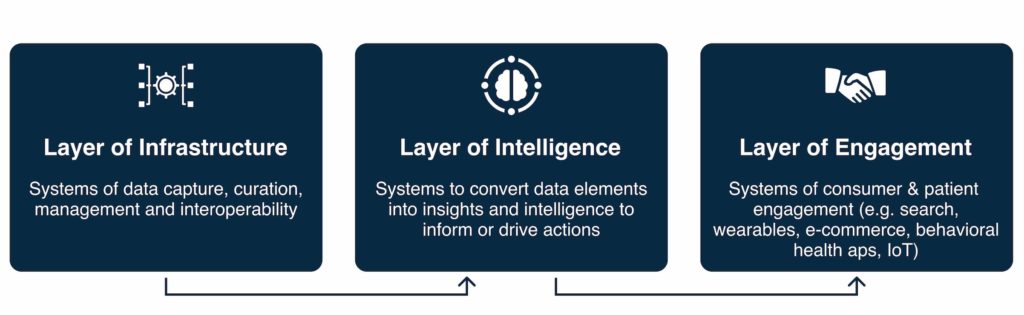
- Infrastructure Layer: basic and consists of data capture, curation, management, storage, and interoperability to create a common data kit upon which the system of healthcare can function.
- Intelligence Layer: built on the Infrastructure layer and converts data to consumable and actionable insights.
- Engagement Layer: enabled by the infrastructure and intelligence layers and curates an end-to-end experience for suppliers who provide services and offerings to patients.
Data liquidity allows access and work with standardized data sets. It is required for the infrastructure layer to serve as the basis for all insights and decisions made in the ecosystem. Data liquidity enables involved parties to operate off the same data sets with increased coordination.
The technology convergence within digitized and connected ecosystems for sharing data across networks and platforms via cloud based applications, e.g. data liquidity, introduces a vast number of new attack vectors for threat actors, weakening cyber security in healthcare.
According to a McKinsey research, 75 percent of experts consider cyber risk to be a top concern across a lot of industries. Due to automation and digitalization, financial companies are not anymore the main target of cybercriminals. Now the threat has become universal.
Some of the top healthcare industry cyber security threats facing the industry include:
- Organizational/ Social attacks: Misleading websites: websites with addresses that are similar to reputable sites are substituted to deceive the user and redirect them to malicious sites. Phishing attacks: mass emails are set from sources perceived as safe and known to obtain sensitive information.
- Malware and ransomware attacks: Used to lock down individual devices, servers and network, many times a ransom is then demanded to unlock the victim’s environment.
- Public Cloud threats: Public Cloud uses a shared security model, and an increasing quantity of health information, such as patient records, is being stored on the cloud. Without proper vulnerability assessments, penetration testing of infrastructure, perimeters, and applications and continuous cybersecurity threat monitoring, cybersecurity healthcare is not strong enough, and health care organizations can suffer data breaches.
- IoMT: Internet of Medical Things or medical devices such as pacemakers and other wearables are often connected to the internet and become exposed to network attack vector exposure. Both the manufacturer that creates the device and the health care facility that delivers or uses devices need to ensure thy have been adequately penetration tested for vulnerabilities at the code level.
- Encryption: it is one of the most critical cyber security issues in healthcare. Encryption is a double edged sword, it is critical for protecting health information, but if all data is encrypted, then it creates blind spots where cyber-attackers can hide from security tools.
How to improve healthcare industry cyber security? Strategies for improving healthcare cybersecurity across the convergence of ecosystem technology stacks
At UnderDefense, we recommend the following to health care providers to combat cyber-threats created by this technology convergence:
- Penetration testing of IoMT and cloud infrastructure environments supporting data liquidity. Evaluating these devices that are connected to the networks for security vulnerabilities is a must for healthcare network security. Public cloud, hybrid cloud and multi-cloud architectures are being utilized at breakneck speed as digital transformation initiatives have been accelerated due to Covid. Platforms and APIs are being integrated across partners such as insurance, employer and other ecosystem partners. These environments are often riddled with vulnerabilities and very often require ethical hacking techniques by Certified Ethical Hackers (CEH) to expose the vulnerabilities a real malicious hacker would find.
- Proper tooling: for strength hospital cyber security posture, we advise our clients in consulting engagements and even contract as a vCISO to ensure InfoSec Governance is established and InfoSec Operational tools are deployed in a layered approach to create as many “hurdles” as possible for a cyber attacker to jump. Network, Application, Endpoint, Perimeter tooling can be used to secure healthcare facilities and although tooling alone is not sufficient, it remains an essential component of a resilient hospital cybersecurity plan.
- Continuously monitoring: 24x7x365 threat detection and responding to events by a team of experts who understand how attackers move through an environment and how to stop or mitigate their impact.
- Continuous education to combat organizational vulnerabilities. Employees shouldn’t become a pain point of cyber security in hospitals. Employees need to be sensitized to the cyber threats and techniques used to lure unwitting users to visit malicious sites or release command and control code on their workstations/ devices. This is a continuous process, because out of 1000 attacks, your organization must be vigilant 1000 times whereas an attacker only has to get by your social defenses once to create business continuity disruption.
- Other practices we endorse and can help implement as part of a resilient cyber security healthcare strategy involve proper file backup plans, proper privilege dissemination, and proper password establishment and management.
















