Supply Chain Cyber Resiliency is emerging as one of the top risk management challenges needing addressed by the InfoSec industry in 2021
By Nazar Tymoshyk
CEO at UnderDefense
Current State of Play
The recent breach of SolarWinds has highlighted the need for a robust supply-chain risk management strategy. There is also a direct impact to the Insurance industry as even one breach can trigger thousands of claims for cyber insurance and forensics services.
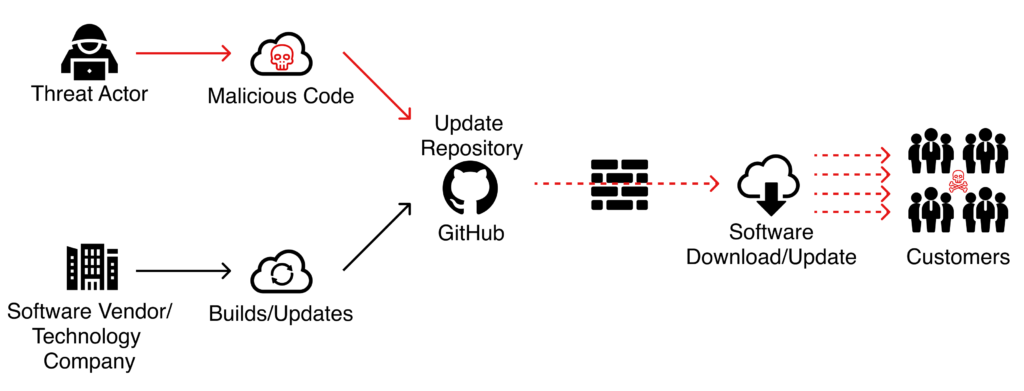
When you combine the cyber-attacks on software, IoT, embedded chips, etc. with the shortage top tier cybersecurity talent in the industry, SolarWinds provides a valuable lens through which we can observe the costs and financial impact to corporations and even prominent organizations such as the US Department of Homeland Security and National Nuclear Security Administration of the United States when lacking a robust supply chain cyber resiliency strategy and executable plan.
Well, this was a brilliant demonstration that Cybersecurity matters, and that such data breaches in cybersecurity really affect the business of all pre-IPO and post-IPO companies:
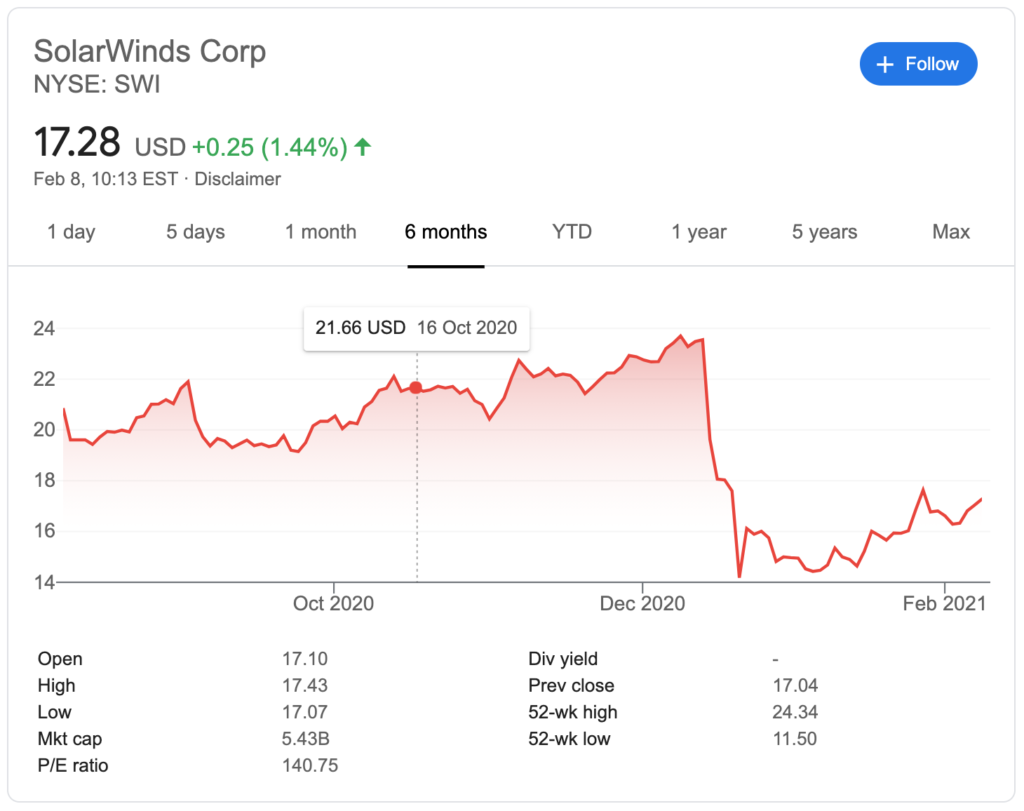
While the SolarWinds breach affected approximately 18,000 organizations who downloaded the trojan, the number of organizations targeted for attacks as a result of the breach is still unknown at this time. We do know that approximately 44 percent of targeted businesses were technology companies, and this fact amplifies the problem even more.

SolarWinds is not alone, Garmin, another well known company, due to unavailability of their application software and infrastructure caused by ransomware attacks, caused millions of their clients to feel the pain driving them to consider changing providers to an alternative.
This highlights the business continuity and financial impact of a breach that brand damage can inflict. Time will tell what impact the SolarWinds attack has on its bottom line.
Ransomware has been a problem since 2015, but now in 2021 the Ransomware players realize that they can gain even more if they remain undetected.
If they can exploit the supply chain through technology firms to implant their tentacles, and then make their move later, a classical worm distribution scenario, their impact is even greater.
Get ready Insurance and HighTech, …you’ll need to be prepared!
The Problem
Predictably, attackers made assumptions and executed a plan of action leveraging these tech companies. The main lesson should be learned from SolarWinds and Garmin cases is that it doesn’t matter how experienced or mature a company is, it can be hacked, directly or more probably in 2021-2025 – through its partners or customers or suppliers. Here are some proof points of the challenge every tech company faces:
- Attackers were undetected for 9 months.
- Software was trusted and whitelisted.
- There was no proper code review because it was rush to CI/CD pipeline.
- Speed, agility and time to market were put above security.
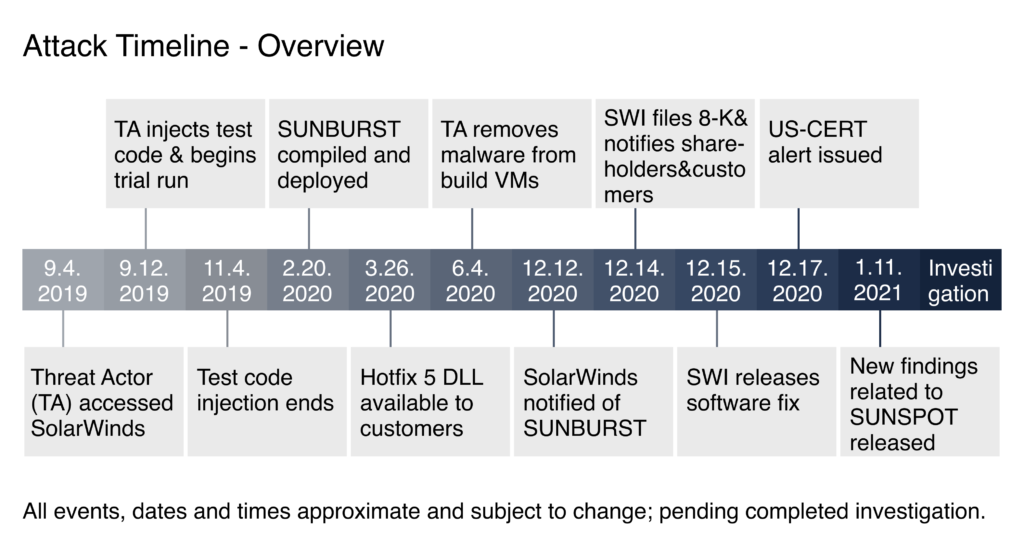
Solarwind was breached and attackers remained undetected for almost 15 months.
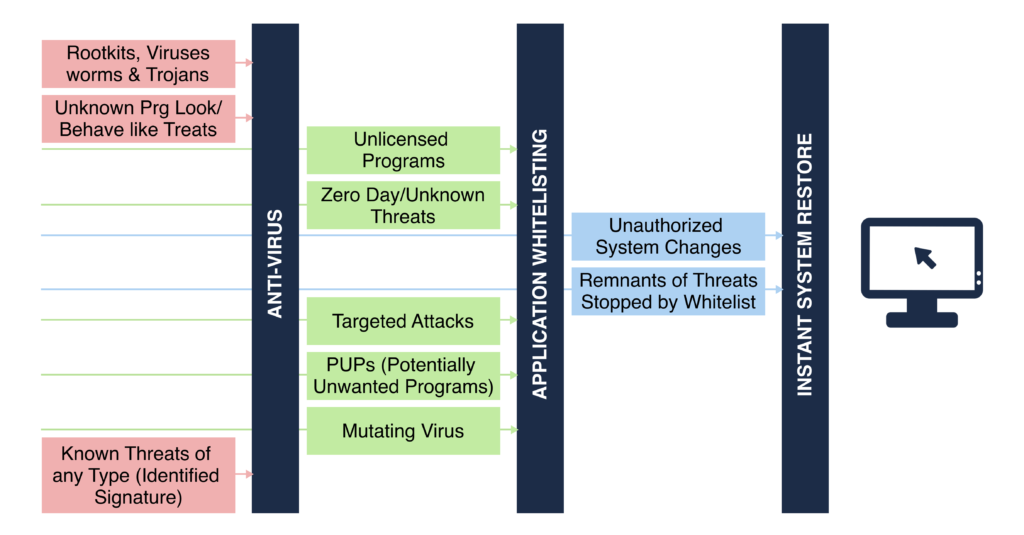
To mitigate such an event, a typical layered security strategy with multiple layers of security hurdles is needed to implement a cyber resilient architecture.
Below are examples of sources from where a supply-chain attack may occur. A compromise and injection of the code through 3rd party (supply chain attack) will impact all customers who use its software.
- Site2Site VPN from partner/outsourcing provider/MSSP.
- Virtual appliance deployed for integration and data pooling from SAP.
- Compromised Product with backdoors.
- Compromised Contractor accounts.
- Outsourcing software development company.
- Outsourced accounting.

The Solution
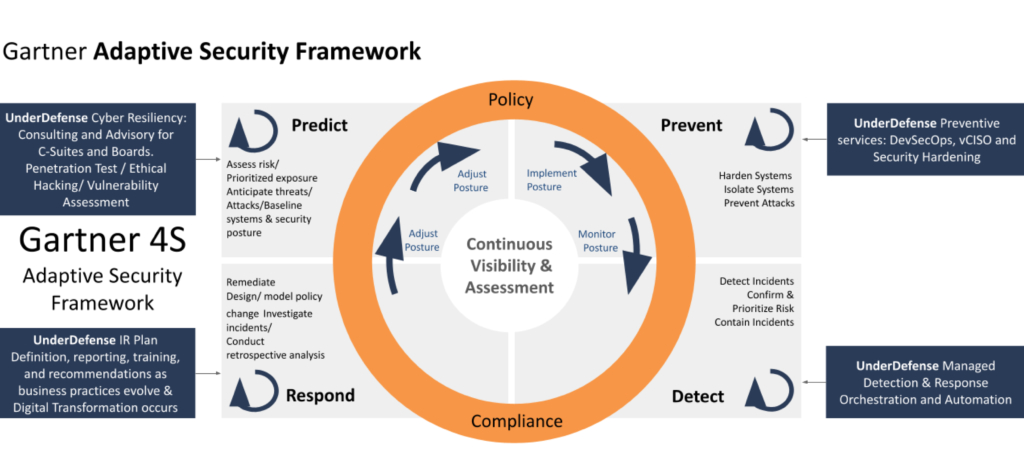
A supply chain is only as secure as its weakest link. Gartner offers a great framework to assure Cyber Resiliency for all the links in the Supply Chain which consists of obvious, but often neglected elements – Predict, Prevent, Detect, and Respond.
At UnderDefense, we have mapped these elements to our services in order to deliver on this framework.
It’s critically important to assure that a company, its partners & vendors are protected adequately. As monitoring and preparation are the keys to this success, UnderDefense recommends the following protective actions:
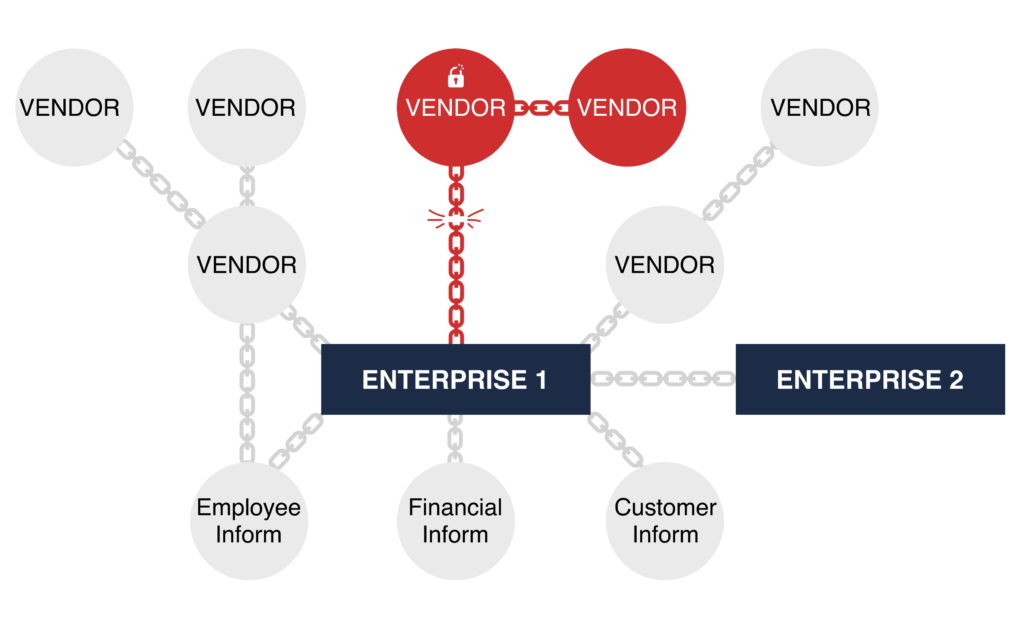
1.Audit, prioritize, segment and isolate.
Prioritization imposes a new perspective on cybersecurity. Prioritization is required to clearly understand which vendors can influence critical data (e.g. access a customer database).
Applying protective measures evenly without considering risk can enable low risk vendor assets to be overprotected, while high risk vendor assets remain dangerously exposed.
2. It’s also important for a company’s security and reputation not to be the weakest link in the chain.

A soft test of organizational security, such as a one time audit, won’t be enough to have a real understanding of the situation.
UnderDefense recommends using security monitoring and other proactive services to ascertain actions that introduce vulnerabilities in a company’s organization continuously.
3. At UnderDefense we emphasize building cybersecurity criteria into the vendor selection process and to negotiate joint policies of cyber risk management and a staff training program with every tier of vendors.
4. Building a Cyber Resiliency program mixed with a DevSecOps set of practices is a cultural shift.
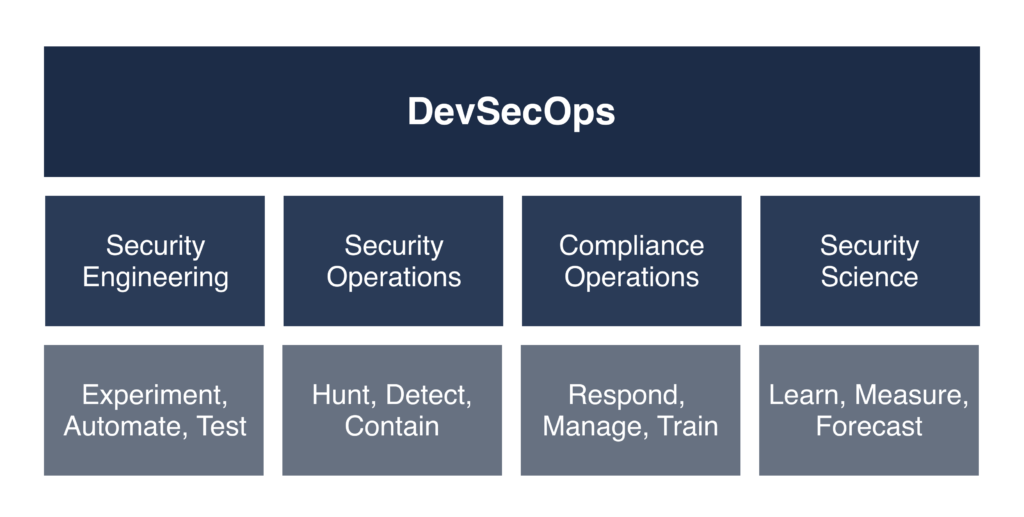
Therefore, as a last step, we recommend implementing a DevSecOps framework where security is at the same level of priority as development and operations, embedding protection from the start, not only reactively after a breach occurs.
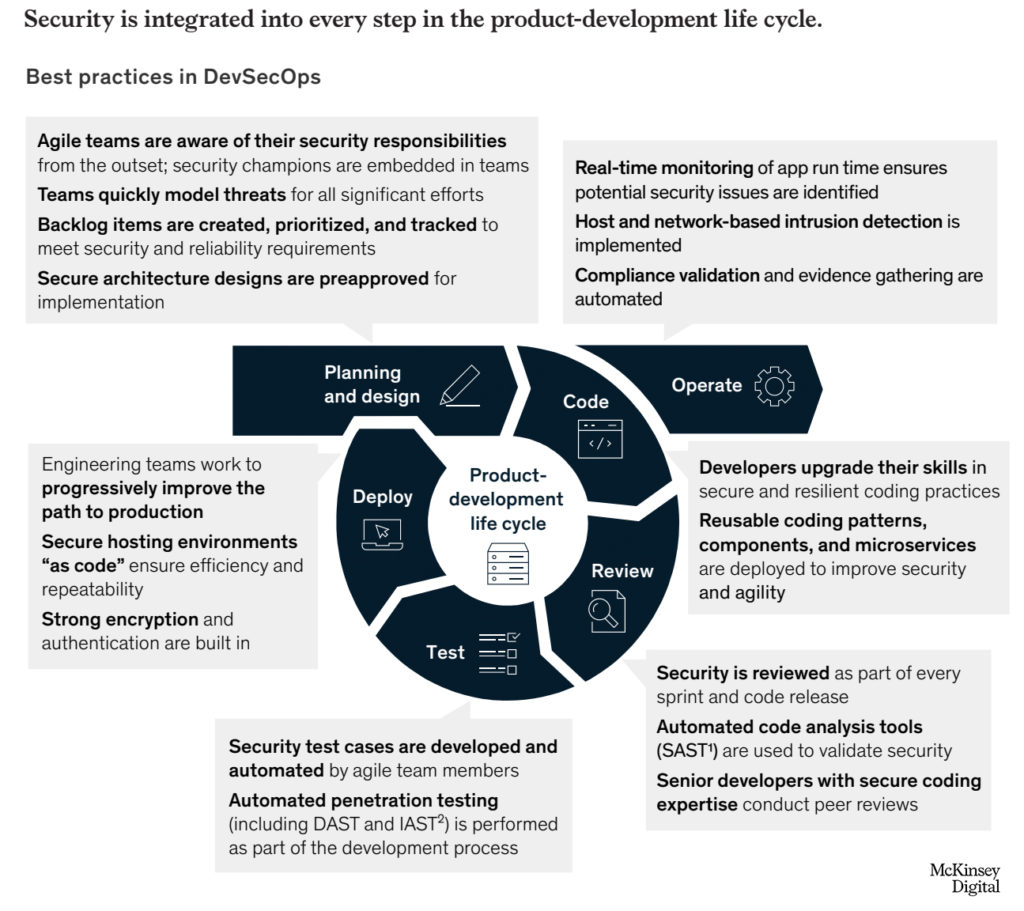
UnderDefense offers coverage for each of these phases.
We recommend to read Gartner`s brochure about DevSecOps integration: How to Seamlessly Integrate Security Into DevOps.
A Final Example
Most people are familiar with Nissan if they don’t actually own one of their vehicles. If you go outside and wait a few minutes, you definitely will see one drive by.
At the beginning of this year, they had a major cybersecurity event. As difficult as it may be to believe, a Nissan Northern America source code leak occurred due to default “admin:admin” credentials. It goes to show that even in a major globally recognized brand and trusted company, if even one person in their enormous workforce uses the “admin:admin” password, it can weaken the entire cybersecurity chain in their company and their partners.
The result, approximately 20 gigabytes of data contained the source code for mobile apps and various tools used by Nissan internally for diagnostics, client acquisition, market research, and NissanConnect services was at risk including data contained in files for companies such as Pepsi, Toyota, SunTech, Motorola, Mediatek, and the U.S. Air Force Research Laboratory.
The Nissan incident demonstrates that there was no “Sec” in their DevSecOps framework. Because the lack of staff training may lead to disaster, cybersecurity organizations should schedule regular check-ins with employees at all levels to explain the relevant cybersecurity threats such as how to recognize a phishing email in order to harden their cybersecurity posture.
















