Recently, the whole gaming world tensed up. One of the largest gaming companies in the USA and Europe faced a massive cyber security breach—hackers have stolen 780 GB of source code for games (such as FIFA, Medal of Honor, Battlefield) of Electronic Arts (EA), a major game publisher.
This incident was very revealing. And in UnderDefense, we see a big problem in the repeatability of such attack scenario. We described the method of how EA sport was compromised and added tips for security program improvement. Following our recommendations, you will be protected from most of the known hackers’ tricks.
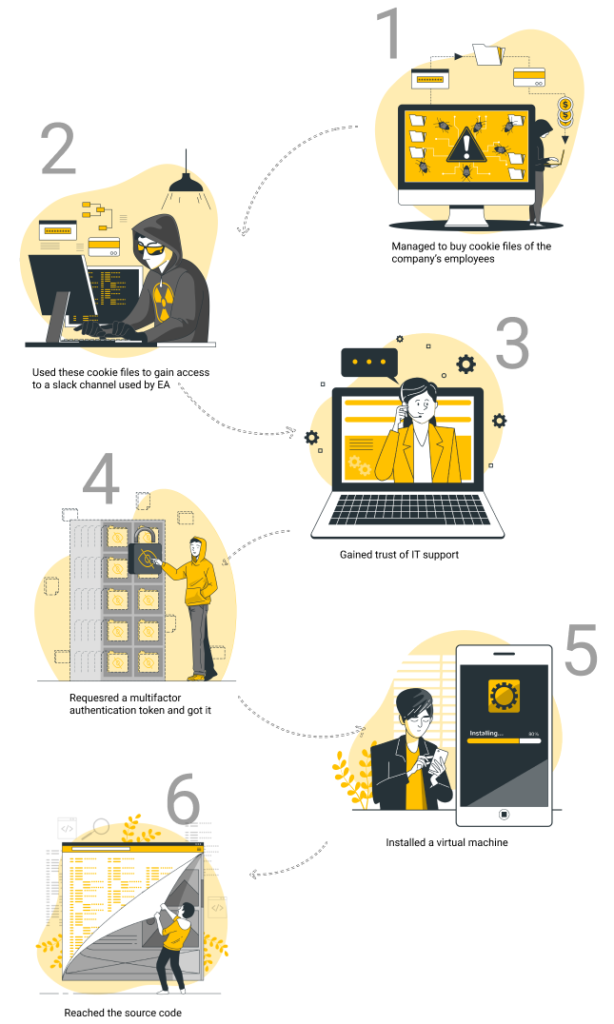
This is what is known to be a social engineering attack, and it’s happening more often than you can ever imagine. As in many other cases, users entrust gaming companies a lot of personal data (including bank card data). Fortunately, EA reported that their users’ data is secure.
UnderDefense has been working with companies in the gaming market for years. We know the value of the system’s availability and customers’ data protection in the IGaming industry. Based on the experience of those customers we are honored to work with, the average downtime of a serious IGaming company costs between 20 and 40 million dollars a day. In the case of EA Games, they said that the attacker had access to their network, downloaded files, but next time in another company, it could be ransomware that will stop critical business operations.
We have conventionally divided the hacker’s path to the core into 5 main stages.
You can ensure protection of your business at every stage, but if you secure all core levels, the business can then be considered to be fully protected.
Let’s take a closer look at each stage.
Stage 1. Staff training
Staff training is everything. Companies should conduct staff training, make it compulsory, and explain its value.
By visiting suspicious websites and using corporate email to log in to other websites, employees might leave cookie files for hackers to use and make the whole company an easy target for malefactors. In the case of EA, employees logged in to the corporate network from personal device. Of course there was no protection from the corporate side and no EDR solution deployed in that home computer. It led to cookies being stolen by malware and then reused by attackers to access sensitive networks.
PROBLEM | SOLUTION |
Compromise of employee’s personal computer | Teach the employees not to log into corporate systems from untrusted (non-corporate) computers. Use a reliable Endpoint Detection and Response solution that covers the whole environment. |
Stage 2. Multi Factor Authentication
Received a password recovery request, the support team must be vigilant and straight. Excessive trust to employees calls is inappropriate. The best idea here is to meet employee personaly or to get some identity confirmation.
PROBLEM | SOLUTION |
Ineffective MFA | Make a strict password recovery process. The support team has to follow the guidance on who should get the recovery and how to identify the authenticity of the employee. |
Stage 3. Security monitoring
Having reliable Managed Detection and Response service provider, all inside activity is insight. Repeatable anomaly activity is typical for user whose account was compromised, and that kind of anomaly should be quickly identified by MDR network analytics. MDR team has to be in place to detect these anomalies, get back to users, check them, and block accounts for future investigation.
PROBLEM | SOLUTION |
Suspicious activity | Companies must know the typical activity of their users to detect anomalies with Managed Detection and Response. Without 24×7 security monitoring company is blind. |
Stage 4. Network segmentation
Imagine that a hacker managed to get passwords and successfully log in to the network. This is where network segmentation comes into play. With delimitation of rights and network segmentation, the hacker could reach only the segment to which the compromised account has access.
PROBLEM | SOLUTION |
Compromised account | If the company uses a jump server, then after authorization, the user gets there, not to the network directly. On the server, the user gets access according to the entrance rights. This is one more level of protection where the extra tools for control might help. |
Stage 5. Monitoring of code changes/ downloads
Even if the hacker has already started uploading data, it still can be noticed and prevented. Traffic control software would show that a high volume of traffic is coming from one host.
PROBLEM | SOLUTION |
High volume of traffic | Traffic control tools are a perfect solution to keep an eye on the suspiciously high volume of traffic and detect its reason with the speed of light. |
To sum up
We advise you to work through each of these stages, because no matter how protected you think your business is, you might have no idea what kind of a skilled and mature hacker is sitting on the other side of the screen. Only multi-layered protection will allow you to sleep calmly.
Your company is held by three equally important pillars: people – tools – processes.
We recommend you to invest money in not just one of these pillars.

Every iGaming company develops its own products. But most of them don’t have Security Monitoring & Threat Hunting. Remember that taking care of your company’s safety, you take care of everyone who trusts you.
UnderDefense’s Security Operations Center offers you continuous monitoring provided with a good team, proven tools, and effective processes. Let’s chat to see how we can help your business stay secure 24x7x365.
By Iryna Yamborska
















