Apple customers believe that no adversaries can hack their personal data or access important files. We bust this myth about perfectly secure MacOS devices! During our Security Awareness training, we demonstrate how anyone can break this system.
Recently we have conducted such training for our customer with a thousand Mac-based computers. Our Antimalware team presented the most common case scenarios of a malware getting on Mac computers and shared tips how do first steps of securing yourself. We covered topic of weak points in MacOS system and showed how the malware exploits these flaws to steal users data.
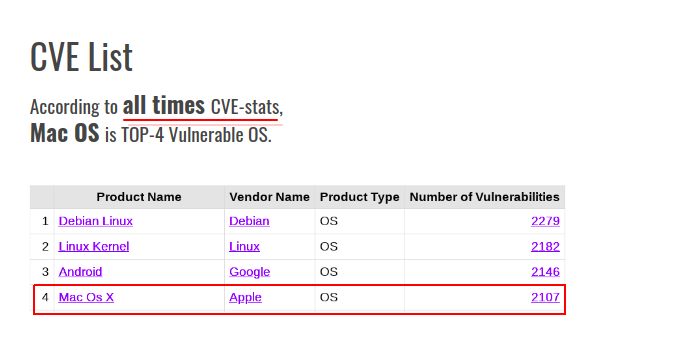
MITRE Corporation has published list of Top 50 the most vulnerable products of ALL TIMES and Mac OS was ranked №4.
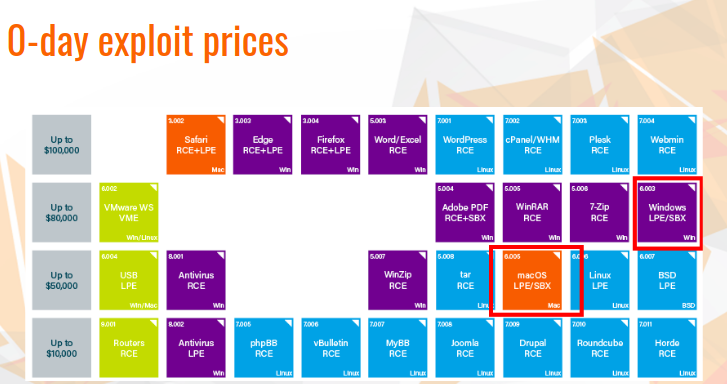
Mac attacks are more specific and dangerous in comparison to other OS. There are more Windows users, however, MacOS hacking cases are more target oriented. At ZERODIUM the price for Mac vulnerabilities is much lower than for Windows. The main aim is to receive access to confidential information.
A well-known is the case about APT group (WindShift), who engaged in highly-targeted cyber-espionage campaigns. They used Mac OS vulnerabilities and custom macOS implants (backdoors) to install a malware on the computer. Likewise, Mac-users must be cautious about viruses that look like PDFs, Word documents (Macros), fake program installers, etc.
Apple assures their clients in best safety policies but still there are weak spots in their defense. As an example, there are browser extensions that are big thread vectors. One tracking extension secretly used the browsing history by collecting UUID and URL links to their own server. Another example is Yesware, a CRM system, that copied the mail body of each message on their server, however, they never mentioned this in their privacy policy and EULA.
In fact, a lot of Safari extensions contain malicious code. Most of them replace user search queries with own fake search URLs, in this way they collect personal data and afterwords shows targeted advertisements.
Most MacOS 10.14 security mechanisms can be easily bypassed with the price of developer’s signature that is usually around 100$. The hacker can sign the virus so that it looks like a legitimate one for a gatekeeper. To avoid this you should install programs only from reliable sources, ex (vendor’s web site).
Request a training for your MacOS users! Contact us to get more details.
View Antimalware MacOS training presentation here.
















