It is not new that COVID-19 pandemic influenced the lives of humanity in the XXI century.
However, it has influenced not only health and economy. Cyber criminals have been quick to exploit the situation of global remote.
According to interview with over than two thousands senior security engineers conducted by CrowdStrike in September and August 2020:
- 71% of these specialists are concerned about ransomware attacks because of COVID-19 the most.
- 27% of those who survived the attack decided to pay the ransom, which in average appeared to be $1.1 million.
- 56% of interviewees reported that their companies suffered such attacks at least once during the last 12 months.
Only after several months companies have realized that they are not ready for the ongoing COVID-19 related cyber attacks and advanced threat actors, who have been developing their skill way longer before the crisis occurred. Cyber Attack protection is now more relevant than ever.
How to protect yourself from cyber attacks in real life?
Fortunately, the threat sharing communities quickly realized the importance of striking back.
Many independent researchers, non-profit organizations, CERTs, as well as other enthusiasts started to collect, aggregate and spread the information related to coronavirus malware campaigns, including but not limited to: phishing emails, malware hashes, suspicious domain names, IP addresses, and even TTPs.
Most organizations decided to share their observations and analysis results via Threat Intelligence platforms with a purpose of quick Incident Response and extensive Threat Analysis. Many of them utilize MISP (malware information sharing platform) for these purposes, that is why we are going to see what can be done using it in a combination with Splunk.
You will find information of how you can set up the environment and use Threat Intelligence gathered from COVID-19 pandemic related Cyber Attacks and protect your business and information below.
These days it’s crucial for a business to be able to review previous and prevent future attacks. The Computer Incident Response Center Luxembourg (CIRCL) kindly created an instance with up to date COVID-19 data, which is hosted on their server, and can provide you with credentials to access it on request.
Practical use-case
How to set up the environment:
Requirements
- Splunk instance.
- MISP (we will use a COVID-19 themed instance).
- MISP42Splunk application.
Features of COVID-19 themed MISP
- A massive community.
- Feeds are already configured.
- No need to host an instance on your own.
- Real-time information about abusing COVID-19.
Prerequisites
- Review the information about COVID-19 MISP here.
- Register with your email for the access to an instance here.
- Install MISP42Splunk from here.
Configure MISP42Splunk on your Splunk instance
- Search for the MISP42 app on the sidebar of your Splunk and click on it.
- Click on the “Create new input” button at the top right corner.
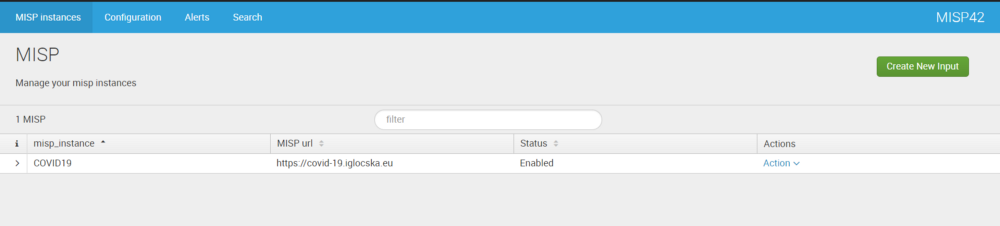
MISP42 interface
- Find “My profile” on a MISP instance under “Global Actions” tab.
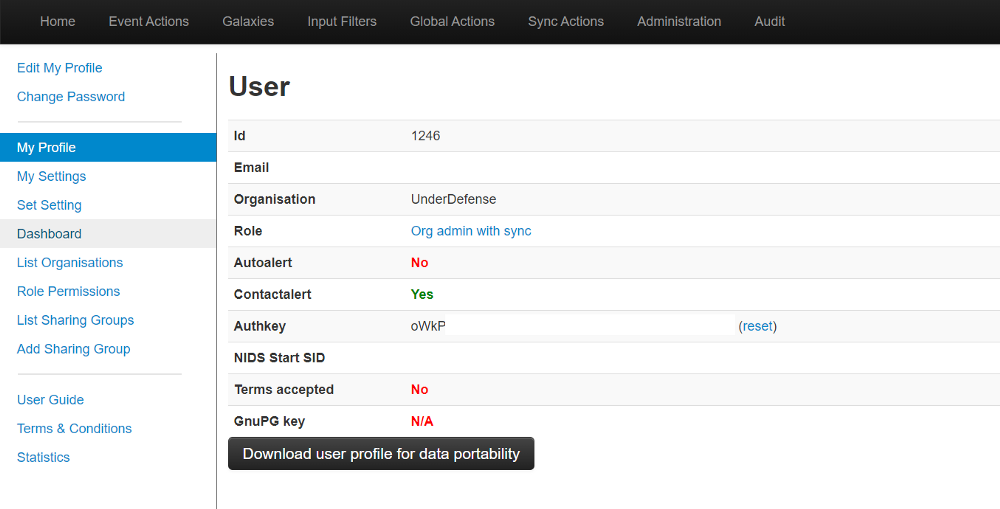
MISP profile settings
- Enter the API key and other credentials in the appropriate fields.
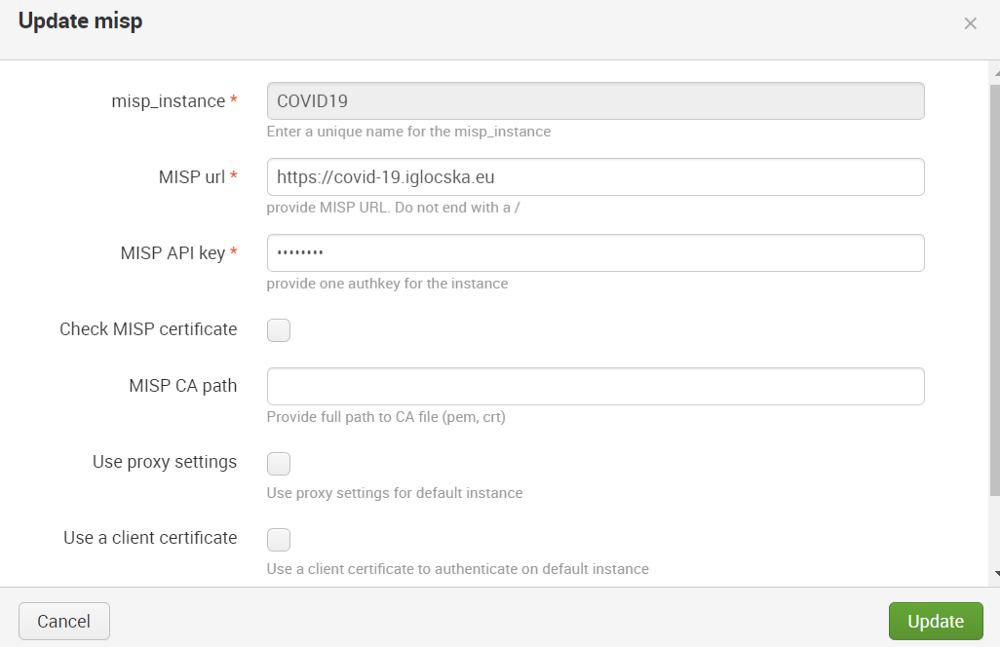
MISP42 settings window
- Check if the events from MISP are synchronized with Splunk.
Basic search to check if everything works:
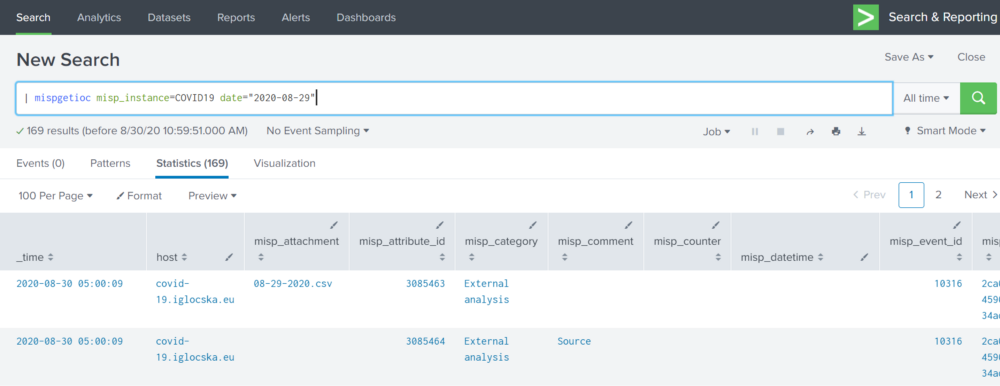
Well done! Now you are ready to move further!
How to use it?
Use Case #1
Use MISP for hashsum collection and correlation with your own findings.
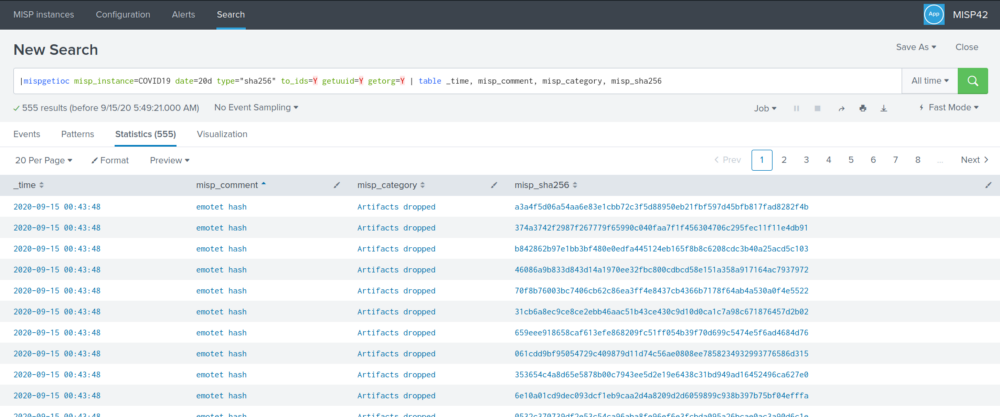
SHA-256 along with the comment and event category.
|mispgetioc misp_instance=COVID19 date=20d type=”sha256″ to_ids=Y getuuid=Y getorg=Y | table _time, misp_comment, misp_category, misp_sha256
This dashboard shows us 555 results for the last 20 days. They include time, comments, category, and hashes belonging to Emotet malware, which is known as a banking Trojan that steals data and spreads through the network. Often it is used as a downloader for other malicious software.
Time column responds for the date when this event was recorded, a comment column tells us which type of intelligence is present in this record, and a category column explains to us which kind of attack does this entry belong to.
Use Case #2
Create a dashboard with inputs to quickly search for IoCs.
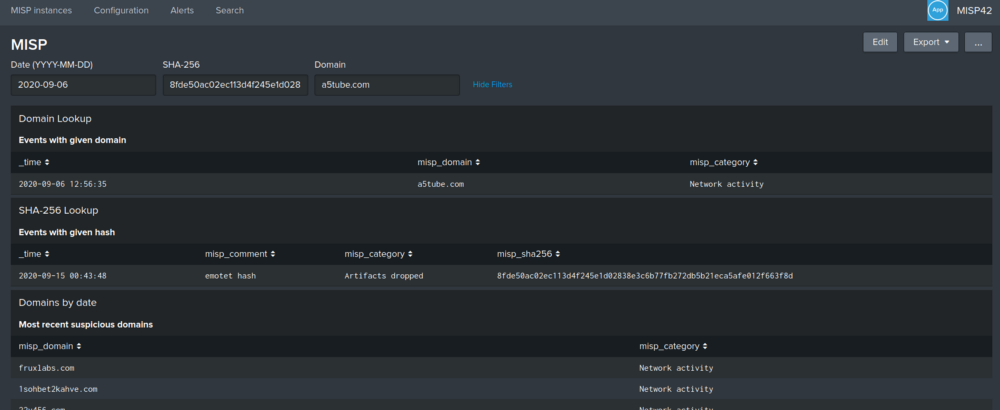
Dashboard view.
The search queries that used here are the following:
|mispgetioc misp_instance=COVID19 date=$ymd_date$ type=”domain,ip-dst,text” to_ids=Y getuuid=Y getorg=Y | search misp_domain=$domain_name$ | table _time, misp_domain, misp_category
|mispgetioc misp_instance=COVID19 date=$ymd_date$ type=”sha256″ to_ids=Y getuuid=Y getorg=Y | search misp_sha256=$sha_256$ | table _time, misp_comment, misp_category, misp_sha256
|mispgetioc misp_instance=COVID19 date=$ymd_date$ type=”sha256,domain,ip-dst,text” to_ids=Y getuuid=Y getorg=Y | table misp_domain, misp_category
Such dashboards can be expanded and therefore help analysts to quickly check a hash or a domain for previous records in MISP threat feeds. Some advanced strategies may include creating a time chart with the domain’s activity or the activity of spreading a file with the given hash.
Summary
Hope, that this article briefly showed you how to set up and use the MISP42Splunk app with an already existing MISP instance.
Sharing the intelligence between companies about ongoing threats has proven its worth mainly in cases when employees receive phishing emails, security analysts detect them and therefore want to warn others.
Using Splunk with MISP can help your organization automate processes of sharing and consuming the information while triggering appropriate actions.
There are also other sources with a lot more detailed examples below for you to examine.
Application’s source code:
https://github.com/remg427/misp42splunk
MISP Summit:
http://archive.hack.lu/2018/misp42splunk_app.pdf
















