Avoid false positives and identify true threats in the vast sea of security logs and alerts your organization generates. Our continuous security monitoring services feature security professionals who are experts at finding the needle in the haystack and delivering an in-depth analysis of your security activities
How we do it:
Apply the Kill Chain Methodology
With Splunk as SIEM in UnderDefense SOC we can help you find indicators of compromised systems and important relationships hidden in your machine data by examining logs from malware analysis solutions, email, and web solutions that represent activities associated with different stages of the kill chain.
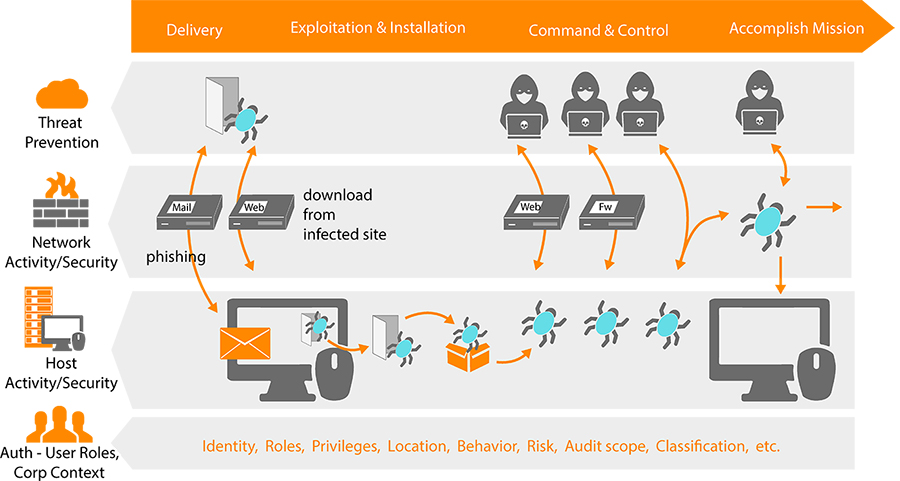
Determine the Scope and Impact of Incidents
Reconstruct the attack sequence by linking events together using any field value to find related events across different security technologies including threat prevention, network security such as email and web gateway, firewalls, endpoint security and endpoint threat detection and response solutions.
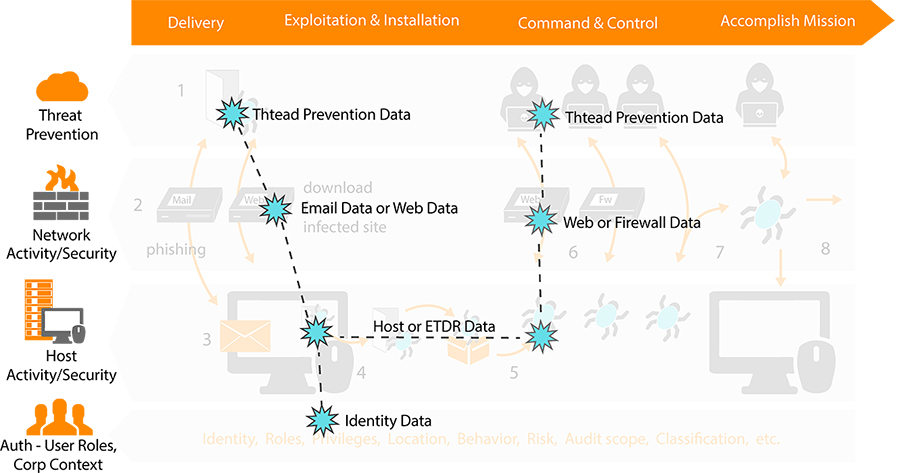
Get End-to-End Visibility into Advanced Threats
Splunk software allows different security teams to collaborate, respond to and defend against advanced threats. Teams can look up, down and across the security and IT technology stack as well as look back in time to find, analyze and respond to activities associated with compromised hosts and advanced threats. Team members can quickly create real-time correlation searches on any activity or condition so that prevention can be incorporated back into the system for continuous monitoring.
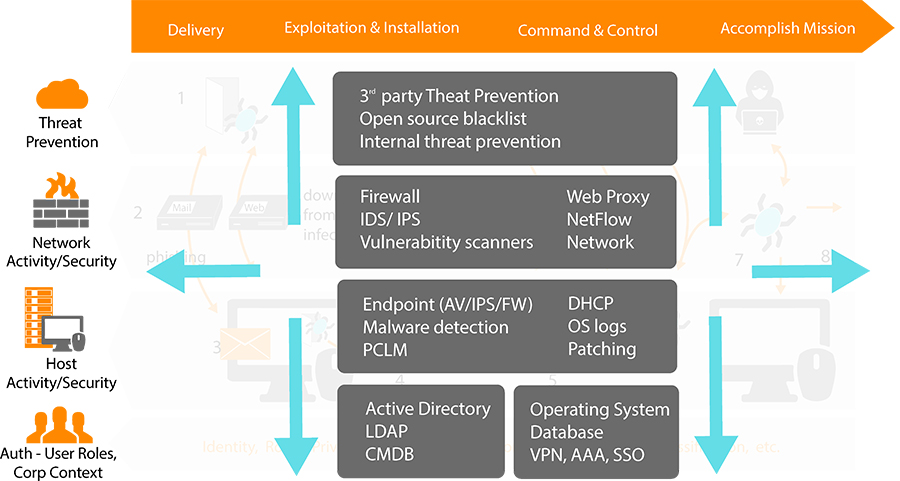
Service details:
duration: 24/7/365 service
value:
- round-the-clock detection
- risk awareness
- trusted expirienced security advisors
- lower costs let small and medium businesses implement Advanced Threat Detection service
- cover a full spectrum of your organization’s security services needs
- unique expertise in red and blue teaming
- quick security breach identification
- better cybersecurity posture
- successful growth of your business
output:
- executive function indivduals operating threat detection service
- incident notification and remediation guidance
- proactive best practices for audit log maintenance and analysis
- compliance reporting
- daily and monthly security reports
- one-on-one security consultation
- add correlation rules
- generate reports for management, auditors
- document results
- conduct post-mortem
- update policies and procedures
applicable:
- IT infrastructure
- Public Web Sites
- Web Applications
- Mobile Applications
- Public/Private Clouds
Why Threat Prevention should matter to your business

Protect your business against targeted attacks
In this day and age its common for organizations to face targeted attacks on their network, that are custom designed to penetrate standard defenses. These targeted attacks can and will monetize private customer data, intellectual property, and possibly even encrypt essential data for ransom.
With UnderDefense on your side you are able to detect, analyze and respond to the hardest hitting ransomware attacks and all of their variants including WannaCry, Petja/NotPetja, BadRabbit.

Know Who, Why, What, Where, When and How
The danger of any attack is that it repeats over time.
Mind-blowing but proven: an invisible “something” can attack and stop your whole business infrastructure’s operations by encrypting the data you hold and entire stack of machines you own. Detect a spreading malware with UnderDefense to prevent the business from falling apart.





